Downloads
 Download
Download




This work is licensed under a Creative Commons Attribution 4.0 International License.
Article
Privacy-Preserving Distributed Entropy Filtering for Microgrids With Innovation Decomposition
Yan Liang 1, Yangkai Chen 2, Dengfeng Pan 3,*, and Haifang Song 2
1 Business School, University of Shanghai for Science and Technology, Shanghai 200093, China
2 Department of Control Science and Engineering, University of Shanghai for Science and Technology, Shanghai 200093, China
3 School of Engineering, Swinburne University of Technology, Melbourne, VIC 3122, Australia
* Correspondence: dengfengpan@swin.edu.au
Received: 31 December 2024
Accepted: 11 March 2025
Published: 25 March 2025
Abstract: Data leakage and cyberattacks are usually inevitable due mainly to the vulnerability of deployed communication networks. The paper proposes a distributed privacy-preserving filter based on the maximum correlation criteria for microgrids. An improved distributed structure is first constructed via adding decomposed innovation from neighbors in update steps. Then, an improved version of the maximum correntropy criterion is defined to evaluate the local filtering performance as well as the consensus performance by adding an innovation-related term. In light of fixed-point iterations and the adopted filter structure, the desired filter gains are obtained recursively by optimizing the proposed index. Furthermore, the profound analysis is performed to disclose that the filtering covariance of external eavesdroppers is larger than target-side filters and hence the privacy of the microgrids can be protected. Finally, an example is exploited to verify its effectiveness.
Keywords:
distributed entropy filtering microgrids innovation decomposition privacy1. Introduction
Low-carbon demands lead to the conversion of fossil energy resources to renewable energy resources, which also changes the energy structure and architecture of energy networks [1]. Moreover, the quality of energy production and transmission is heavily influenced by various factors, including the environment, climate, people's activities, and accidental events [2]. To enhance reliability and safety, SCADA systems should undergo the development and application of new filtering and control theories and techniques such that the impact of the above mentioned factors can be effectively restrained. As one of the fundamental theories, reliable and efficient distributed filtering is essential in practical engineering to obtain dynamic internal states of microgrids [3−8].
Classical approaches to system monitoring include weighted least squares (WLS)-based algorithms, Kalman-type algorithms, and stability-based algorithms in the field of microgrids [9]. WLS-based algorithms are suitable for the state estimation of steady smart grids and its essence is an optimization solver to find a suitable vector to minimize the difference between actual and estimated measurements. According to dynamic systems described by a state-space model, Kalman filtering and its extended version have gained universal recognition and wide applications because of their robust, real-time, and user-friendly execution capabilities[10−11]. For instance, an outlier-suppressed Kalman filter has been adopted in [12] to acquire microgrids' operating states. A novel “consensus+innovation” based algorithm proposed in [13] can realize the filtering accuracy obtained by centralized least squares estimators if connectivity can be guaranteed. However, Gaussian assumption of noises, which could not be satisfied in many actual engineering systems, shackles the applications of developed filtering algorithms. In other words, non-Gaussian noises could lead to performance degradation and even instability of filtering algorithms[14]. As such, some interesting filtering algorithms based on various entropy criteria, have been generated in the past few years for the systems suffering from general noises without any restriction in their distribution, see [8, 12, 15−16]. For instance, an anomaly-resistant filter based on local and edge measurements has been provided in [8] for wide-area power systems by resorting to the unscented transformation and a fixed-point iteration. A correntropy-based filter has been developed in [15] for nonlinear complex networks with uncertain dynamical bias.
Different from Kalman-based filtering, adopted kernel functions in correntropy indicators can provide high-order statistics of stochastic variables benefiting from the map from the low-dimensional space to the high-dimensional one. In the past few years, some interesting entropy filtering schemes have been developed based on different criteria, including minimum error entropy and maximum correntropy [17−20]. Generally specking, maximum-correntropy filters own excellent filtering performance in presence of outliers or heavy-tailed impulsive noises [21], while minimum-error-entropy filters can effectively handled the challenges caused by multi-modal noises [22]. When the distribution paradigm is a matter of concern, a popular structure of filters is to add the latest neighbor estimation into prediction steps. Obviously, the added part is generally handled as a known vector, which greatly reduces the challenges of covariance calculation and gain design. However, the aforementioned entropy criteria, evaluating local errors of both states and measurements, are incapable of effectively guaranteeing the filtering consensus. As such, one of the motivations is to develop an entropy index to overcome such shortcomings. It should be point out that the construction of consensus-related terms in a potential index is nontrivial if the transmission of neighbor information is affected by unknown variables. Furthermore, gains of distributed filters cannot be easily received in the consensus-based filtering framework. In addition, the corresponding filtering algorithms should not rely on cross-covariance to meet plug-and-play requirements.
Distributed entropy filtering cannot be separated from the information exchanges among filters. Recently, some interesting filtering approaches have been developed in [23−25] for systems subject to diverse physical constraints and communication restrictions. It is worth mentioning that deployed networks are usually open and vulnerable. Although a great deal of necessary protection has been executed, data leakage and cyberattacks, like ringworm, are still hard to be shaken off [26−27]. The consequence caused by this phenomenon is usually enormous economic loss, negative social impact, as well as damage of national security. Recently, several privacy-preserving methods have been proposed using by encryption, watermarking, and perturbation addition strategies. Under perturbation addition strategies, data security is generally guaranteed by injecting noises into sensitive data (forming ciphertexts) to maximize the distortion of eavesdroppers' inference. For instance, the security has been effectively improved by a watermarking-based strategy in [28] and by a noise-addition-based rule in [29]. It is important to acknowledge that the current fashion approaches display essential weaknesses in calculation burden, filtering performance, or relying on a trusted third party. In order to possibly reduce the potential risk of privacy leakage, it is crucial to develop straightforward privacy-preserving strategies suitable for microgrids, which is another reason why our research is necessary. As an alternative, state decomposition can render the locally real data indiscernible by eavesdroppers by resorting to a simple arithmetical operation.
With the help of the above analysis, the paper devotes itself to developing a distributed secure filter with privacy-preserving such that the leakage of crucial data for microgrids can be effectively avoided while the filtering performance is not seriously compromised. To this end, two critical difficulties have to be overcome: 1) how to construct an innovation-decomposition-based filter in a distributed way to ensure the privacy; and 2) how to find an entropy index to cater to the evaluation of consensus-type distributed filters. The main contributions are outlined as follows:
1. a novel privacy-preserving filter in a distributed framework is constructed for microgrids via an innovation decomposition rule;
2. a new maximum correntropy criterion (MCC) index is provided by adding a quantized term about the innovation received from the neighbors;
3. carefully mathematical analysis is put forward to obtain the desired filter gains with the help of fixed-point iterations; and
4. the profound investigation is performed to disclose that the filtering covariance of external eavesdroppers is larger than target-side filters and hence the privacy of the microgrids can be protected.
The structure of this paper is organized as follows: Section 2 displays the problem formulation including microgrid models and constructed filters. Section 3 presents the performance of the proposed filtering, including the gain design under MCC as well as privacy analysis. A illustrative simulation is given to demonstrate the effectiveness of the proposed algorithm in Section 4 and the conclusion is given in Section 5.
Notations. The notation used throughout the paper is fairly standard. denotes the identity matrix of compatible dimension. For a matrix , and represent its transpose and inverse, respectively. The shorthand diag denotes a diagonal matrix. denotes the -dimensional Euclidean space.
2. Problem Formulation
2.1. The model of microgrids and the constructed filter
As the presentation in [30], a discretized version of microgrids in the rotating -frame can be modeled by
where the stacked state vector is usually selected as , the known input is , and the measurement is collected by sensor . The vectors and are non-gaussian noises with mean , and covariance and , respectively. The system matrices are and dependent on a given sampling period , and matrices and being the same with ones in [30]. stands for the predetermined measurement matrix and stands for the set of sensor nodes. Here, and describe the real and imaginary components of the variable , which could be , , or standing for the terminal voltage of voltage source converters, the voltage of common coupling points, and the currents of both series filter and transmission line . Finally, stochastic noises and and initial state are usually assumed to be irrelevant.
To monitor the dynamic behavior of the above microgrids, the following accessible filter on target sides is constructed:
where () is the ideal innovation acquired from its neighbors and itself, and and denote one-step prediction and estimate, respectively. and are the filter gains to be acquired.
For the purpose of privacy protection, the ideal innovation needs to be decomposed as
where obeying the uniform distribution and are two time-varying and interdependent stochastic scalar sequences and play the role of dynamical private keys. Furthermore, the parameter is also private for all external eavesdroppers. It should be pointed out that such two scalars are accessible only for the filter itself. Under such a scenario, the actual filter on target sides can be organized as follows:
where is the actual exchanged data among neighbors and could be eavesdropped by external eavesdroppers. The framework of the addressed filtering issue can be found in Figure 1.
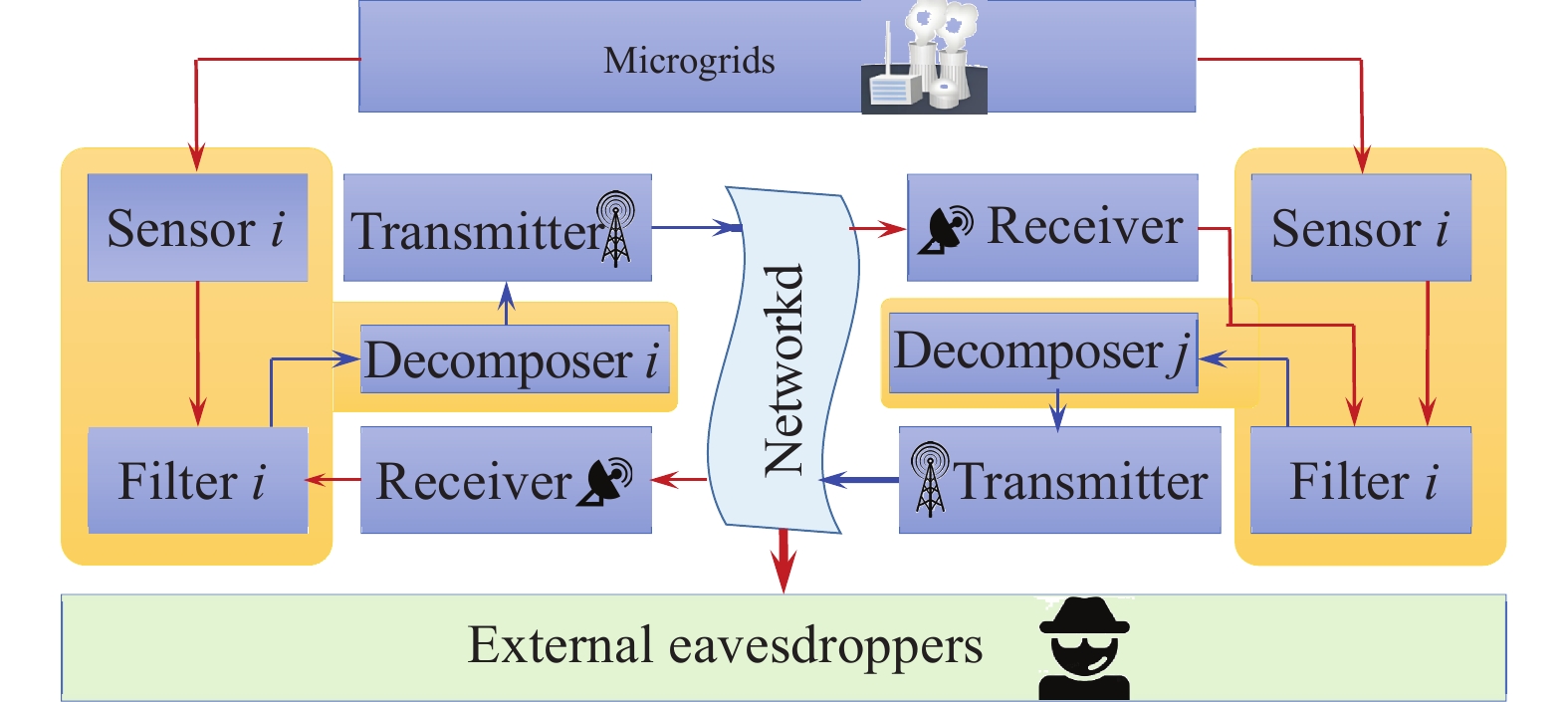
Figure 1. The framework of the addressed filtering issue.
2.2. The aim of this paper
To evaluate the impact from non-Gaussian noises, this paper employs the following improved MCC
with , and , where , , and are three predetermined weighting coefficients, the matrices and are, respectively, acquired by the decomposition and , and is the traditionally generalized Gaussian density kernel function.
In summary, this paper addresses the privacy-preserving entropy filtering issue based on innovation decomposition under non-Gaussian environments. Specifically, the main purpose is to acquire the desired filter gains () under a distributed way such that the dynamic behavior of the considered microgrid is effective monitored while the state and measurement information is private for eavesdroppers. That is to say, the estimated state by the distributed filter is unbiased and the MCC is maximized for the designed gains , while this obtained estimate is private if external eavesdroppers only collect the decomposed innovation () and then performs
where means the eavesdroppers' estimate.
In summary, let us provide two quantitative evaluation metrics about privacy.
Definition 1 For the data set until instant received by both systems and eavesdroppers, if the relationship
holds, then the adopted privacy strategy is said to achieve secrecy, where the system and the eavesdropper should use the greatest similar rule except for the inaccessible private key.
Definition 2 For the data set until instant received by both systems and eavesdroppers, if the relationship
holds, that is, the eavesdropper's estimation is biased, then the adopted privacy strategy is said to achieve secrecy, where the system and the eavesdropper should use the greatest similar rule except for the inaccessible private key.
Remark 1 In comparison with (4), the gap in (5) reflects in the lacked term, resulting in a large filtering variance, which is just the essence of privacy protection of the proposed innovation decomposition. Such privacy is also regarded as the relative secrecy defined in [31]. Furthermore, the calculation cost of the adopted privacy strategy is lower than homomorphic encryption and state decomposition and hence satisfies the real-time requirement of filtering algorithms.
Remark 2 In the past few years, some interesting algorithms of privacy-preserving Kalman filtering have been developed, focusing on a) the privacy conditions [32−33], b) the trade-off between systems and eavesdroppers' performances[34−35], and c) the quantized privacy leakage [36]. For instance, a trade-off index has been proposed in [35] by scheduling the transformation matrix depending on the solution of an optimization issue with constraints. Furthermore, the bound of the privacy leakage has been acquired in [36] with a hybrid privacy policy based on state decomposition and noise injection. Different from these existing results based on filtering variance, our paper employs the correntropy indicator to evaluate the filtering performance benefiting from its capability of involving high-order statistics of stochastic variables and hence is more suitable for the case in the presence of outliers or heavy-tailed impulsive noises. Furthermore, the quantized privacy leakage is disclosed by resorting to matrix analysis.
Remark 3 From the viewpoint of the adopted protection mechanisms, privacy-preserving strategies can be roughly divided into three categories[37−39], that is, i) the cryptography-based approach, ii) the perturbation-injected approach, and iii) algebraic transformation-based approaches. The mechanism of the first approach lies in that eavesdroppers cannot effectively decrypt the information due to the ack of a crucial encryption scheme or private keys. The idea of the second approach security is to maximize the distortion of eavesdroppers’ inference or bring into indistinguishability between real data and inferred ones. The last one benefits from the introduced transformation maps playing the role of a mask. The adopted method in our paper can be regarded as an algebraic transformation approach, and the transformation map is just a linear one .
3. Main Results
This section focuses on acquiring a distributed design method of privacy-preserving filters under the improved MCC index. To this end, let us introduce errors
and the corresponding decomposition
Obviously, and describe the private and public estimation errors, respectively.
3.1. Gain design under MCC
According to the introduced decomposition, one has the following two error dynamics
and
In accordance with (6)-(7), one can easily verify
which means the estimates are unbiased. In what follows, the covariance matrices of one-step prediction errors are derived as
Furthermore, according to , one has
or equivalently
Obviously, it exposes the relationship among , and . Now, let us provide the ideal weight in the MCC index for the subsequent gain design.
Theorem 1 For the constructed distributed filter (4) with private and public error dynamics (6) and (7), the estimated states are unbiased and the covariance and satisfying the initial conditions and are, respectively, bounded by and , which can be iteratively updated by
and
where . Furthermore, the filtering error covariance and of the distributed filter (4) are respectively bounded by and satisfying
Proof. Let us derive the variance and . In light of the error dynamic (6), one can calculate
Similarly, it can be easily derived from the error dynamic (7) for the filter that
Considering scalability, the above equation can be handled as follows
Furthermore, one has the bounds and governed by (8) and (9), respectively. Finally, noting the relationship between and , and considering the received matrices and result in the upper bound (10), which ends the proof.
The above theorem provides the upper bound of filtering error covariance, which serves as the weight of MCC to perform normalization. In what follows, let us select the suitable gain matrix to maximize such an MCC index. To this end, introducing row vector with the th element being and other elements being zero, the MCC index can be reorganized as follows
Introduce the notations
with being or for convenience, and then denote
as the values of and determined by the -th iterative calculations at instant . According to the conception of fixed point iteration, one has the following theorem.
Theorem 2 For the constructed distributed filter (4) with private and public error dynamics (6) and (7), the covariance matrices and are bounded by and via (8) and (9). For the prefixed step size , the MCC index is optimized when the filters gains are selected as and () with
where
Proof. Setting results in
which can be reorganized by
Furthermore, the above equation can be dealt with as follows
which means
where
Compared to (4) and (11), one has
which make the MCC index maximal. However, it follows from , and that these two gains highly depend on the real-time estimate and thus cannot be directly calculated. Inspired by [20], one can access a computable version via a fixed-point iterative approach, which completes the proof.
Remark 4 In this theorem, to obtain the gains, the approximation is employed for in , and . As such, the optimality of MCC cannot be realized due to the requirement of limited step size in actual execution. Furthermore, the adopted MCC includes the term in comparison with traditional ones. As such, the index can be regarded as an improved version of MCC.
3.2. Privacy analysis
It should be pointed out that (5) does not include the term in comparison with the structure (4) due to the privacy of . In Theorem 1, one discloses that the filter (4) is unbiased and hence can be satisfied. In what follows, let us discuss the privacy of the established filtering scheme from two cases: a) the external eavesdroppers having the initial unbiased estimate, (i.e. ), and b) the external eavesdroppers having the initial biased estimate, (i.e. )
a) Case on
Under this case, it is not difficult to verify that the external eavesdroppers can also receive a unbiased estimate via the scheme (5) with any filter gains and . Now, let us analyze the validity of eavesdroppers's scheme, that is, discussing the bound of filtering error covariance.
It should be noted that external eavesdroppers do not know the adopted decomposition strategy, and hence usually regard all acquired innovation as normal one. Similar to (9), considering the filter dynamic (5), eavesdroppers can acquire the incorrect error covariance
which lead to the upper bounds
On the other hand, one can obtain the relationship via the conditions developed in Theorem 1 as follows
which means
in the mean square sense, where and are taken into account.
Similarly, one cannot difficulty derive that
which yields
with
Considering the expectation
one can conclude that the symmetric matrix is positive definite in the mean square. Furthermore, compared (12) to (13) and (14), the filtering covariance of external eavesdroppers is larger than object-side filters when they take the same gains, i.e. . According to Definition 1, the privacy of the developed filtering scheme can be guaranteed.
b) Case on
The case means that the external eavesdroppers cannot capture the initial valid estimate. Denote the initial deviation and the eavesdropping error . In light of (5), one has
which means that eavesdroppers only acquire a biased estimate and hence the privacy can be guaranteed undoubtedly for a limited time. Furthermore, by resorting to the analysis of case a), it can be inferred that the filtering covariance of external eavesdroppers is also larger than the filters on target sides when they take the same gains, i.e. . According to Definition 2, the privacy of the developed filtering scheme can be guaranteed.
Combining the above two cases, one has the following conclusion.
Theorem 3 For the innovation decomposition strategy (3) adopted in target-side filters (4), when external eavesdroppers take the same gains (i.e. ) and perform the estimation algorithm (5) on eavesdropper sides, the filtering of external eavesdroppers could be biased and the corresponding filtering covariance is larger than target-side filters, and hence the information of target states is effectively protected.
Remark 5 In this paper, a novel privacy-preserving filtering scheme is developed in the framework of MCC indicators. Different from traditional structures that neighbouring information is adopted in prediction steps, our structure employs neighbouring decomposed innovation in update steps to improve the filtering performance. The challenges from such a nontrivial structure is intelligently handled via introducing an improve MCC indicator. Furthermore, the profound analysis is proposed to disclose that the filtering covariance of external eavesdroppers is larger than target-side filters and hence the filtering accuracy are distinctly reduced.
4. Simulation Results
An example is utilized in this sections to show the effectiveness of the designed filtering algorithm based on innovation decomposition. This engineering plant comprises two power generation units with the same physical parameters in [30] and the deployed SCADA owns four sensors whose corresponding communication is the same one in [3]. Furthermore, the noise intensity are set as , and . The weights , and in the employed MCC index are selected as , and , and the positive scalars , and are prefixed as , and in the utilized kernel function . For the calculation of the upper bound , the parameter is selected as , and the initial values of some matrices are predetermined by . Finally, for the purpose of security, the four pairs of time-varying sequences () are generated via Matlab Software and plotted in Figure 2.
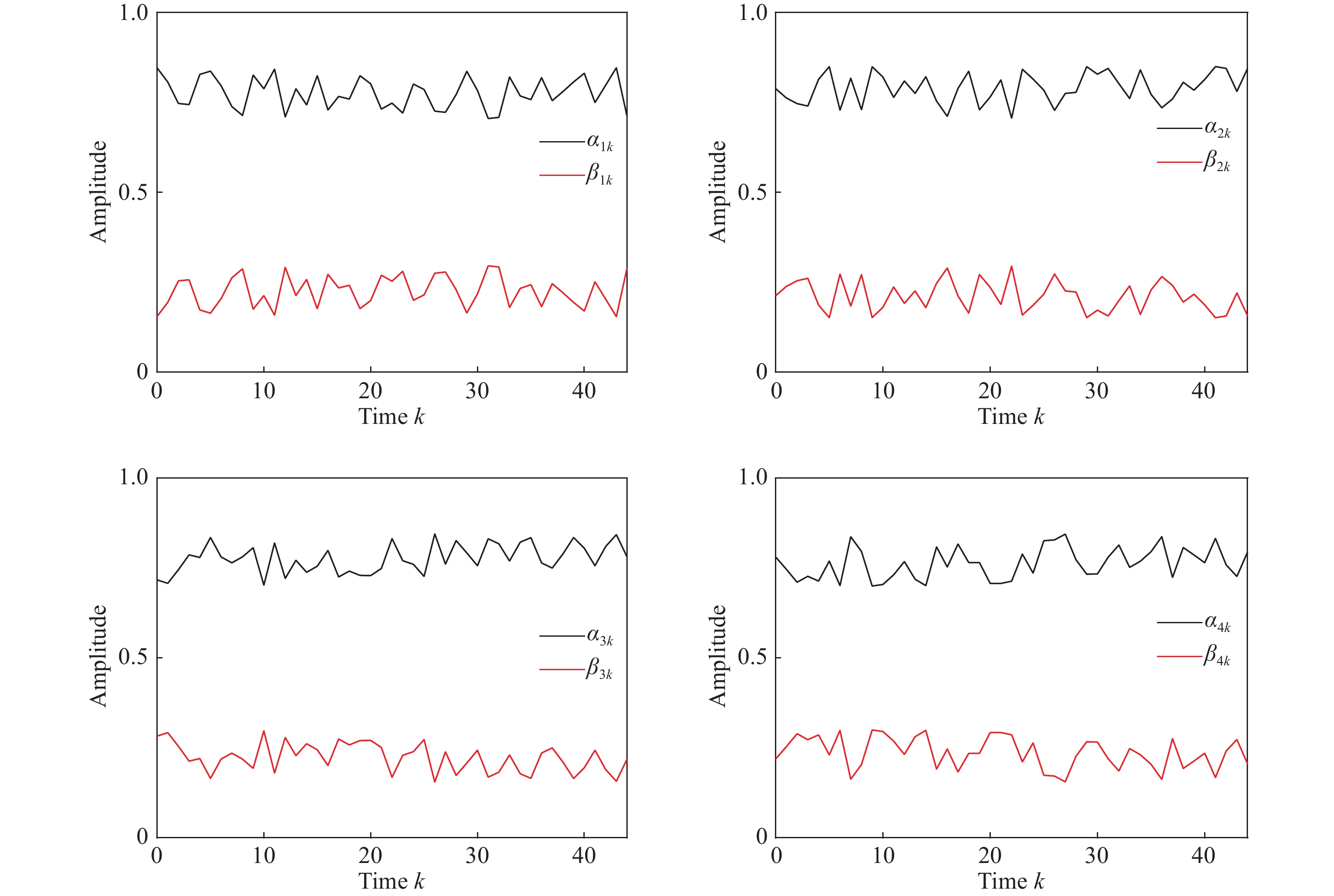
Figure 2. Time-varying sequences for innovation decomposition.
Now, let us discuss both the filtering performance and the privacy of the develop filter. Assume that eavesdroppers can easily capture all parameters except for . In light of the above setting, the simulation outcomes are demonstrated in Figure 3 and Figure 4 for estimated states and eavesdropped ones, where the subscript in or stands for their -th component. It is not difficult to see from these two figures that the gap between the real state (black lines) and the eavesdroppers' state (blue lines) is obviously larger than that between the real state and estimated ones (red lines). As such, the developed privacy rule make the capability of eavesdroppers dramatically recused.
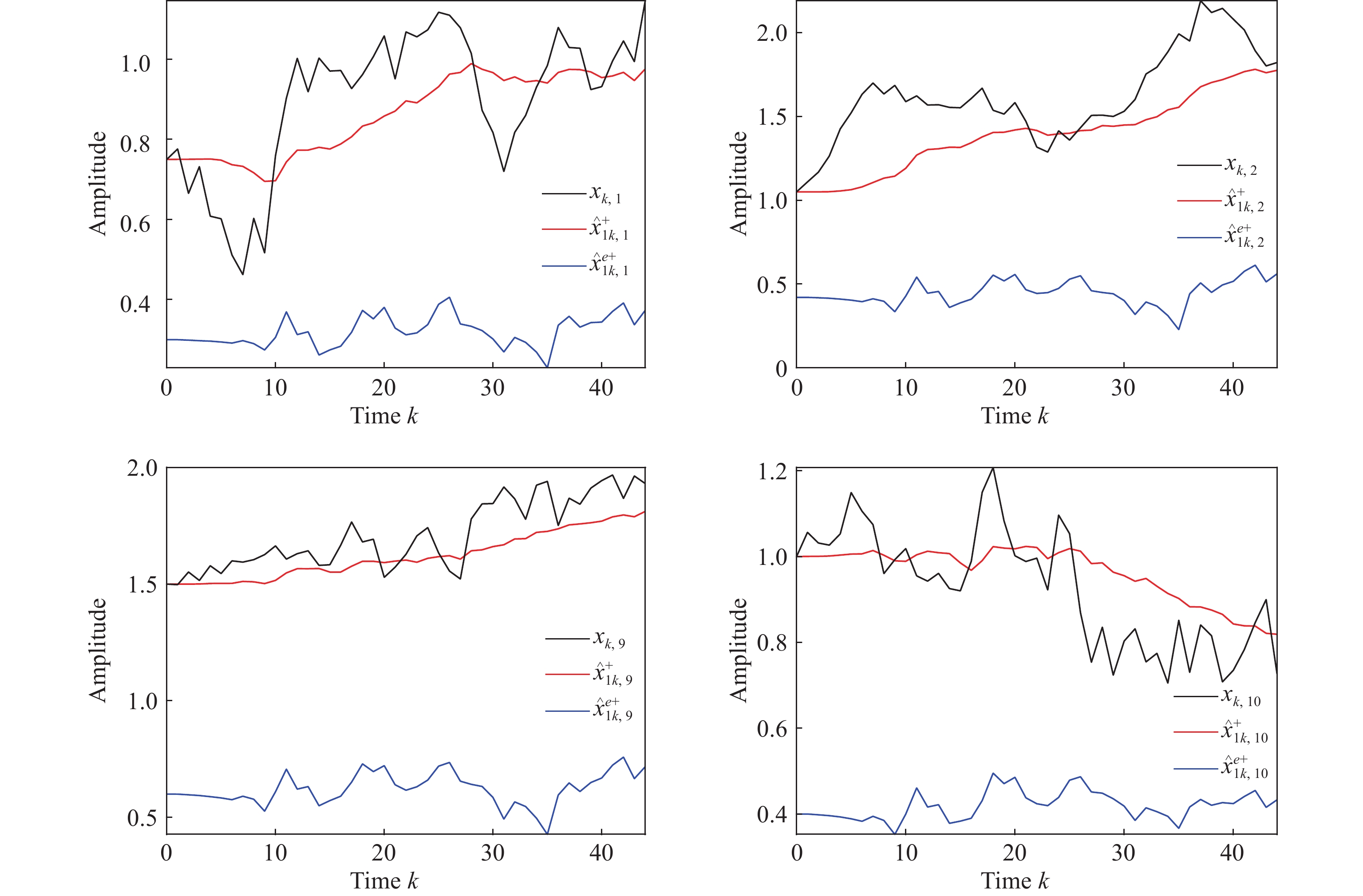
Figure 3. Actual state and its estimate by filter 1 and eavesdroppers.
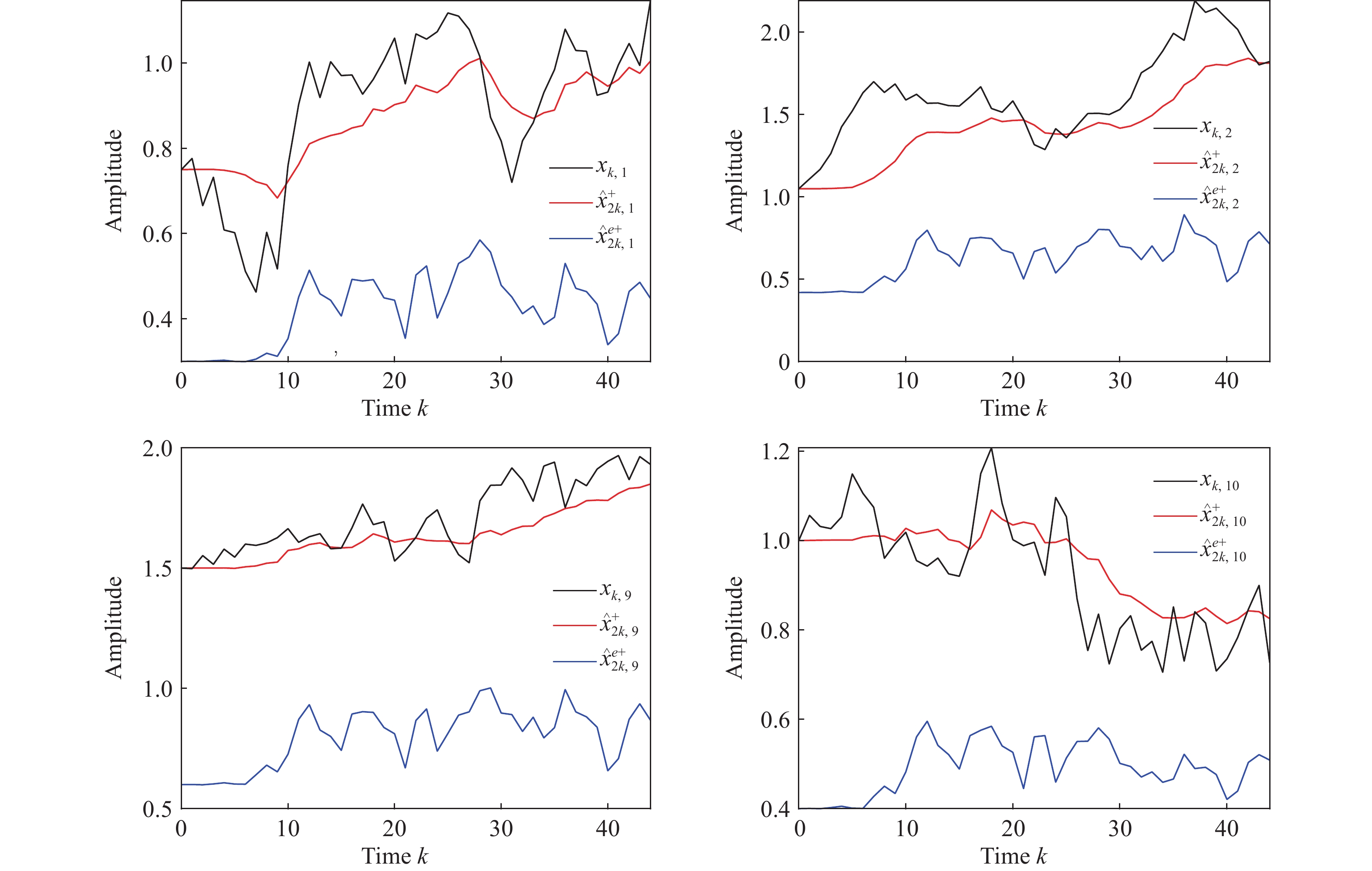
Figure 4. Actual state and its estimate by filter 2 and eavesdroppers.
5. Conclusions
In this paper, a distributed privacy-preserving filtering algorithm has been developed via an improved MCC index, in which a quantized term about the innovation received from the neighbors has been introduced to evaluate local filtering performance as well as consensus performance. In light oft the constructed filter structure, the desired filter gains have been resolved recursively in a distributed way. Finally, an example has been exploited to verify its effectiveness. Future research directions will include, but not limited to, the developments of advanced filtering schemes with hybrid privacy policies, consensus fusion rules or different entropy indexes [38, 39, 40].
Author Contributions: Yan Liang: conceptualization, methodology, writing -original draft preparation; Yangkai Chen and Haifang Song: investigation, methodology; Dengfeng Pan: writing-reviewing and editing. All authors have read and agreed to the published version of the manuscript.
Funding: This work is supported by the National Natural Science Foundation of China with Grant No. 62373251.
Data Availability Statement: Not applicable.
Conflicts of Interest: The authors declare no conflict of interest.

References
- Yan, M.Y.; Shahidehpour, M.; Alabdulwahab, A.; et al. Blockchain for transacting energy and carbon allowance in networked microgrids. IEEE Trans. Smart Grid, 2021, 12: 4702-4714. doi: 10.1109/TSG.2021.3109103
- Thale, S.S.; Wandhare, R.G.; Agarwal, V. A novel reconfigurable microgrid architecture with renewable energy sources and storage. IEEE Trans. Ind. Appl., 2015, 51: 1805-1816. doi: 10.1109/TIA.2014.2350083
- Zhao, P.F.; Ding, D.R.; Dong, H.L.; et al. Secure distributed state estimation for microgrids with eavesdroppers based on variable decomposition. IEEE Trans. Circuits Syst. I: Regul. Pap., 2024, 71: 3307-3316. doi: 10.1109/TCSI.2024.3357523
- Su, G.H.; Wang, Z.L. Event-triggered robust integrated observer design for nonlinear interconnected system based on multiple intermediate estimators. IEEE Trans. Circuits Syst. II: Express Briefs, 2024, 71: 3443-3447. doi: 10.1109/TCSII.2024.3362711
- Hu, X.H.; Peng, C.; Shen, H.; et al. Extended dissipative scalable control for AC islanded microgrids. IEEE Trans. Circuits Syst. I: Regul. Pap., 2023, 70: 5421-5432. doi: 10.1109/TCSI.2023.3305525
- Dai, D.Y.; Li, J.H.; Song, Y.H.; et al. Event-based recursive filtering for nonlinear bias-corrupted systems with amplify-and-forward relays. Syst. Sci. Control Eng., 2024, 12: 2332419. doi: 10.1080/21642583.2024.2332419
- Wu, Q.; Song, Q.K. Isolated industrial micro-grid demand response with assembly process based on distributionally robust chance constraint. Int. J. Syst. Sci., 2024, 55: 2211-2223. doi: 10.1080/00207721.2024.2337901
- Qu, B.G.; Wang, Z.D.; Shen, B.; et al. Anomaly-resistant decentralized state estimation under minimum error entropy with fiducial points for wide-area power systems. IEEE/CAA J. Autom. Sin., 2024, 11: 74-87. doi: 10.1109/JAS.2023.123795
- Wang, Y.; Liu, H.J.; Tan, H.L. An overview of filtering for sampled-data systems under communication constraints. Int. J. Netw. Dyn. Intell., 2023, 2: 100011. doi: 10.53941/ijndi.2023.100011
- Rana, M.M.; Li, L.; Su, S.W.; et al. Consensus-based smart grid state estimation algorithm. IEEE Trans. Industr. Inform., 2018, 14: 3368-3375. doi: 10.1109/TII.2017.2782750
- Chen, T.P.; Cao, Y.H.; Chen, X.B.; et al. A distributed maximum-likelihood-based state estimation approach for power systems. IEEE Trans. Instrum. Meas., 2021, 70: 1002110. doi: 10.1109/TIM.2020.3024338
- Qu, B.G.; Wang, Z.D.; Shen, B.; et al. Outlier-resistant recursive state estimation for renewable-electricity-generation-based microgrids. IEEE Trans. Industr. Inform., 2023, 19: 7133-7144. doi: 10.1109/TII.2022.3205354
- Kar, S.; Hug, G.; Mohammadi, J.; et al. Distributed state estimation and energy management in smart grids: A consensus + innovations approach. IEEE J. Sel. Top. Signal Process., 2014, 8: 1022-1038. doi: 10.1109/JSTSP.2014.2364545
- Zhao, H.Q.; Long, X.Q.; Hou, X.Y.; et al. Simplified set-membership augmented affine projection generalized maximum complex correntropy criterion algorithm. IEEE Trans. Circuits Syst. II: Express Briefs, 2024, 71: 3623-3627. doi: 10.1109/TCSII.2024.3365212
- Song, W.H.; Wang, Z.D.; Li, Z.K.; et al. Maximum correntropy filtering for complex networks with uncertain dynamical bias: Enabling component-wise event-triggered transmission. IEEE Trans. Neural. Netw. Learn. Syst., 2024, 35: 17330-17343. doi: 10.1109/TNNLS.2023.3302190
- Chen, B.D.; Liu, X.; Zhao, H.Q.; et al. Maximum correntropy Kalman filter. Automatica, 2017, 76: 70-77. doi: 10.1016/j.automatica.2016.10.004
- Yin, X.; Zhang, Q.C.; Wang, H.; et al. RBFNN-based minimum entropy filtering for a class of stochastic nonlinear systems. IEEE Trans. Automat. Contr., 2020, 65: 376-381. doi: 10.1109/TAC.2019.2914257
- Feng, Z.Y.; Wang, G.; Peng, B.; et al. Distributed minimum error entropy Kalman filter. Inf. Fusion, 2023, 91: 556-565. doi: 10.1016/j.inffus.2022.11.016
- Dang, L.J.; Chen, B.D.; Xia, Y.L.; et al. Dual extended Kalman filter under minimum error entropy with fiducial points. IEEE Trans. Syst., Man, Cybern.: Syst., 2022, 52: 7588-7599. doi: 10.1109/TSMC.2022.3161412
- Song, H.F.; Ding, D.R.; Shen, B.; et al. Jointly distributed filtering based on generalized maximum correntropy criterion: Memory-based event-triggered cases. IEEE Trans. Industr. Inform., 2023, 19: 10024-10033. doi: 10.1109/TII.2022.3231429
- Chen, B.D.; Xing, L.; Zhao, H.Q.; et al. Effects of outliers on the maximum correntropy estimation: A robustness analysis. IEEE Trans. Syst., Man, Cybern.: Syst., 2021, 51: 4007-4012. doi: 10.1109/TSMC.2019.2931403
- Chen, B.D.; Dang, L.J.; Gu, Y.T.; et al. Minimum error entropy Kalman filter. IEEE Trans. Syst., Man, Cybern.: Syst., 2021, 51: 5819-5829. doi: 10.1109/TSMC.2019.2957269
- Lin, C.H.; Wu, W.C.; Guo, Y. Decentralized robust state estimation of active distribution grids incorporating microgrids based on PMU measurements. IEEE Trans. Smart Grid, 2020, 11: 810-820. doi: 10.1109/TSG.2019.2937162
- Ao, W.; Song, Y.D.; Wen, C.Y. Distributed secure state estimation and control for CPSs under sensor attacks. IEEE Trans. Cybern., 2020, 50: 259-269. doi: 10.1109/TCYB.2018.2868781
- Wang, W.; Ma, L.F.; Rui, Q.Q.; et al. A survey on privacy-preserving control and filtering of networked control systems. Int. J. Syst. Sci., 2024, 55: 2269-2288. doi: 10.1080/00207721.2024.2343734
- Ma, S.Z.; Wen, G.H.; Luan, M.; et al. Privacy-preserving distributed optimal economic-emission dispatch over directed graphs. IEEE Trans. Circuits Syst. II: Express Briefs, 2024, 71: 3418-3422. doi: 10.1109/TCSII.2024.3361085
- Zhang, L.X.; Zhang, K.; Jiang, H.Y. Attack-free protocols design for leader-following consensus of discrete-time multi-agent systems with multiple input delays. Int. J. Syst. Sci., 2024, 55: 407-425. doi: 10.1080/00207721.2023.2272301
- Zhou, J.Y.; Yang, W.; Ding, W.J.; et al. Watermarking-based protection strategy against stealthy integrity attack on distributed state estimation. IEEE Trans. Automat. Contr., 2023, 68: 628-635. doi: 10.1109/TAC.2022.3171422
- Fan, B.; Wang, X.F. Distributed privacy-preserving active power sharing and frequency regulation in microgrids. IEEE Trans. Smart Grid, 2021, 12: 3665-3668. doi: 10.1109/TSG.2021.3067142
- Riverso, S.; Sarzo, F.; Ferrari-Trecate, G. Plug-and-play voltage and frequency control of islanded microgrids with meshed topology. IEEE Trans. Smart Grid, 2015, 6: 1176-1184. doi: 10.1109/TSG.2014.2381093
- Kennedy, J.M.; Ford, J.J.; Quevedo, D.E.; et al. Innovation-based remote state estimation secrecy with no acknowledgments. IEEE Trans. Automat. Contr., 2024, 69: 7433-7448. doi: 10.1109/TAC.2024.3385315
- Zou, J.Y.; Liu, H.X.; Liu, C.; et al. Optimal privacy-preserving transmission schedule against eavesdropping attacks on remote state estimation. IEEE Control Syst. Lett., 2024, 8: 538-543. doi: 10.1109/LCSYS.2024.3398200
- Das, N.; Bhattacharya, R. Privacy and utility aware data sharing for space situational awareness from ensemble and unscented Kalman filtering perspective. IEEE Trans. Aerosp. Electron. Syst., 2021, 57: 1162-1176. doi: 10.1109/TAES.2020.3038243
- Huang, J.; Gao, C.; He, X. Privacy-preserving state estimation with unreliable channels. ISA Trans., 2022, 127: 4-12. doi: 10.1016/j.isatra.2022.05.035
- Song, Y.; Wang, C.X.; Tay, W.P. Privacy-aware Kalman filtering. In
Proceedings of 2018 IEEE International Conference on Acoustics, Speech and Signal Processing, Calgary, 15–20 April 2018 ; IEEE: New York,2018 ; pp. 4434–4438. doi: 10.1109/ICASSP.2018.8462600. - Moradi, A.; Venkategowda, N.K.D.; Talebi, S.P.; et al. Privacy-preserving distributed Kalman filtering. IEEE Trans. Signal Process., 2022, 70: 3074-3089. doi: 10.1109/TSP.2022.3182590
- Chen, W.; Wang, Z.D.; Hu, J.; et al. Differentially private average consensus with logarithmic dynamic encoding-decoding scheme. IEEE Trans. Cybern., 2023, 53: 6725-6736. doi: 10.1109/TCYB.2022.3233296
- Chen, W.; Liu, G.P. Privacy-preserving consensus-based distributed economic dispatch of smart grids via state decomposition. IEEE/CAA J. Autom. Sin., 2024, 11: 1250-1261. doi: 10.1109/JAS.2023.124122
- An, W.J.; Ding, D.R.; Dong, H.L.; et al. Privacy-preserving distributed optimization for economic dispatch over balanced directed networks. IEEE Trans. Inf. Forensics Secur., 2025, 20: 1362-1373. doi: 10.1109/TIFS.2024.3438129
- Sun, L.; Ding, D.R.; Dong, H.L.;
et al . Distributed economic dispatch of microgrids based on ADMM algorithms with encryption-decryption rules.IEEE Trans. Autom. Sci. Eng .2025 , in press. doi: 10.1109/TASE.2024.3485922.







