Downloads
 Download
Download




This work is licensed under a Creative Commons Attribution 4.0 International License.
Article
Torus-Event-Based Sliding Mode Control for Networked Interval Type-2 Fuzzy Systems Under Deception Attacks
Xingwang Liu 1, Zhi Ling 2,*, and Yang Zhang 2
1 College of Electrical and Power Engineering, Taiyuan University of Technology, Taiyuan 030024, China
2 School of Automation, Nanjing University of Science and Technology, Nanjing 210094, China
* Correspondence: Lingzhi@njust.edu.cn
Received: 21 November 2023
Accepted: 29 June 2024
Published: 25 March 2025
Abstract: In this paper, the security control problem is investigated for the discrete networked interval type-2 (IT2) fuzzy system under limited communication resources. A torus-event-triggering protocol is developed via two thresholds to regulate the transmission of data, ensuring avoiding the transmission of abnormal data. The deception attacks considered are assumed to have the ability of injecting false information into the data transmitted between sensor and controller. By constructing the new membership functions, a security sliding mode controller is proposed and the theoretical analysis proves that the stochastic stability of the closed-loop system and the reachability of the prescribed sliding surface can be guaranteed. Finally, an illustrative numerical example is proposed to demonstrate the effectiveness of the proposed control strategy.
Keywords:
interval type-2 (IT2) fuzzy systems sliding mode control (SMC) cyber attacks torus-event-triggering1. Introduction
Since originally put forward by L.A.Zedeh [1] in 1965, the study of systems has so far achieved significant progress over the last few decades, from perspectives of both theoretical research and practical applications. Nowadays, the fuzzy theory could find extensive utilization in such as system control, pattern recognition, signal processing and decision analysis, see [2–5] for instance. It should be mentioned that proposed in 1980s, the well known T-S fuzzy model (which was named after Takagi and Sugeno) is capable of globally approximating nonlinear systems in terms of a series of linear submodels with certain appropriately selected fuzzy weights. Moreover, such an approximation can achieve arbitrary precision over any convex compact set, see, e. g. [6, 7]. It should be pointed out that, nevertheless, the traditional T-S fuzzy model approach cannot be adopted to characterize nonlinear systems subject to structure variations and parameter uncertainties, due to the difficulty in designing exact membership functions (MFs). Accordingly, it gives the rise to the study on interval type-2 (IT2) T-S fuzzy model that has the ability to use bounded membership functions to describe the parameter uncertainties [8–11]. However, such special membership functions will inevitably bring difficulties for the performance analysis as well as controller design. Up to now, quite a few control strategies have been presented, including but not limited to, state feedback control [12, 13], output feedback control [14, 15], and sliding mode control (SMC) [16–18], etc.
In modern industrial engineering, a large part of systems can be described as cyber-physical systems (CPS), such as smart grid [19] and internet of vehicles (IoV) [20, 21]. One of the key features of CPSs is the integration of computation module and physical processes via networks such as internet, which makes it very vulnerable to cyber-threats. Among them, the cyber-attacks are recognized as the main menace [22–25] and therefore has attracted considerable attention from either the aspect of attack detection [26] or the perspective of security control [18, 27–29]. There have been so far several attack forms that are frequently applied in practical engineering, among which the most two popular are the so-called denial-of-service (DOS) attacks and deception attacks. Note that the deception attack could manipulate the targeted systems by injecting false data into original ones while keeping stealthy, and it thus is recognized as one of the most powerful and applicable attack forms. As such, recently, in the context of deception attacks, the corresponding security control issue for fuzzy systems has aroused the interest of many researchers [30, 31]. Specifically, an adaptive torus-event-based fuzzy control approach was proposed in [30] for the fuzzy system, when the system state contains the false information injected by the attackers. When facing both actuator failure and deception attacks, an event-triggered dynamic output feedback controller was designed in reference [31] for T-S fuzzy system.
Recently, a special type of communication technique (event-triggering mechanism) has gained growing interest that could help alleviate the burden on communication resource. In practical engineering, it is usually very difficult to achieve a balance between the communication cost and the control/estiamtion performances, owing to the fact that better performance always demands higher cost [32]. In the context of networked control system, the issue on how to reduce the communication frequency while maintaining satisfactory performance has become a hot spot. An applicable technique is to introduce protocols to regulate the process of information transmission [33–35], as a special case of which the event-triggering scheme has become more and more popular. Such a scheme schedules the data transmission by comparing certain system-related values with the validating conditions to seek the triggering instants (the time steps the data are permitted to be sent) [36–38]. It should be emphasized that, however, all the aforementioned even-triggering mechanisms are designed on basis of the unilateral triggering, which means that the data will be sent once the triggering condition is validated, regardless of the data quality. Nevertheless, the real-world systems under operation are always confronting unusual situations such as measurement outliers and malicious attacks, which makes the data abnormal and obviously, not suitable for usage. Accordingly, a two-side event-triggering scheme (called torus-event-triggering mechanism) was developed in [39], which has the ability to mitigate the effects resulting from the abnormal data. The main idea behind such a mechanism lies in that the triggering indices of a normally operating system should reside within a certain range characterized by a two-side inequality condition, and neither too large nor too small values should trigger the condition. Up to now, however, the research on security control of fuzzy system in combination with the torus-event-triggering mechanism has been far from enough.
It is widely acknowledged that the sliding mode control (SMC) method is an effective algorithm with strong robustness, which has been found extensive successful application in practical engineering. With the help of its strong robustness, the SMC technique is utilized in this paper to design a security controller for the IT2 fuzzy system based on torus-event-triggering scheme and subject to deception attacks. The main contributions of this paper are summarized as follows: 1) The torus-event-triggering mechanism and deception attacks are considered simultaneously, where the two-side event-triggering mechanism could effectively help reduce the influence of abnormal measurement data caused by attacks. 2) A security sliding mode controller for the new IT2 fuzzy system subject to deception attacks is proposed, ensuring the stochastic stability of the closed-loop system and the reachability of the prescribed sliding surface.
Notation: The notation used here is fairly standard except where otherwise stated. denotes the dimensional Euclidean space. stands for the expectation of the stochastic variable . describes the Euclidean norm of a vector . represents the transpose of . denotes the identity matrix of compatible dimension. The notation (respectively, ), where and are symmetric matrices, means that is positive semi-definite (respectively, positive definite). stands for a block-diagonal matrix whose diagonal blocks are given by . The symbol in a matrix means that the corresponding term of the matrix can be obtained by symmetric property. means the trace of matrix and represents the sign function.
2. Problem Formulation
2.1. System Description
Consider the following -rule IT2 fuzzy systems:
Rule: IF is and... and is , THEN
where represents the th premise variable, and is the number of the fuzzy sets; represents the th fuzzy set in the th IF-THEN rule and is the number of the fuzzy rules; , and are known system matrices with appropriate dimensions; , , stand for the system state, control input and output; The firing strength of the th fuzzy rule is defined as follows:
with the lower and upper membership functions
where and denote the lower and upper membership grades of in fuzzy set , which satisfy .
Then the overall IT2 fuzzy system can be formulated by
with the MFs satisfying , and
2.2. Torus-event-triggering mechanism and deception attacks
For the purpose of relieving the communication burden, torus-event-triggering mechanism is utilized to reduce the communication frequency. Suppose that the releasing instants is obtained iteratively by
where , is the current measurement and is the measurement at the latest triggering instant. stands for the triggering threshold matrix. are the lower and upper bounds of the torus events.
Then the triggered measurement signals will be send to the controller, and the zero-order holder is applied to hold the signals until a new measurement is achieved. Suppose the available signals without cyber attacks for controller are
When the triggered measurement is transmitted to the controller via an open network, it may be attacked by the adversary. In this paper, deception attacks are considered, which can be described as follows:
where is a stochastic variable with the expectation
and .
Assume that there is a known matrix , and the deception attack satisfies .
The purpose of this article is to design a desired security IT2 fuzzy controller to attain the stochastic stability of the system (3) under the torus-event-based communication protocol and deception attack.
Definition 1[40]: The IT2 fuzzy system (3) is stochastically stable for any initial condition if
Remark 1. In this paper, the torus-event-triggering mechanism is adopted with the purpose of mitigating the effects from abnormal data. It is known that the traditional event-triggering scheme is always designed to send the data only when the difference between the sent data and sampling data becomes sufficiently large (characterized by the triggering threshold). The fact behind such an idea is that data with decided changes are more worthy of being transmitted. However, in practice, many cases such as measurement outliers and cyber attacks would make the data abnormal and inappropriate for subsequent usage. Under the framework of conventional triggering scheme, these abnormal data could easily validate the triggering condition as they always change abruptly and obviously. The traditional one-side triggering mechanism cannot properly handle such abnormal situations. Accordingly, in this paper, due to the existence of deception attacks, we apply the two-side event-triggering scheme (i.e., torus-event-triggering mechanism) to mitigate the effects resulting from the abnormal data.
3. Main results
3.1. Sliding Mode Controller Design
Choose the following sliding function:
where is a given matrix.
According to the torus-event-triggering mechanism and deception attacks, it is obvious that only corrupted discrete data can be received by controller. Then the sliding mode controller for the IT2 fuzzy systems when is designed as follows:
Rule: IF is and... and is , THEN
where is the th fuzzy gain and represents the number of the fuzzy rules for the fuzzy sliding mode controller. is acquired by replacing in (9) with . is a positive scalar. Thus the overall fuzzy sliding mode controller can be written as:
where is the new membership function constructed for the controller:
with and .
For simplicity, , and are denoted as , and . Substituting the fuzzy sliding mode controller (11) and (6) into the IT2 fuzzy system (3), we can acquire the following closed-loop IT2 fuzzy system for :
with .
3.2. Stochastic stability analysis
Theorem 1: If there exist matrices , scalar , satisfying
with
for , and , the closed-loop IT2 fuzzy system (12) is stochastically stable.
Proof: Choose the following Lyapunov function:
It follows that
Noting that , For , from the expressions (12), one has
By using , we have
On the other hand, under condition (13), it has
By introducing the torus-event-triggering mechanism conditions, for , it has
Combining (16)-(20), we can obtain
where .
Under the condition (14), it has
Therefore, there exists a sufficiently small scalar such that
Taking expectation for both sides of (23), it has
By adding up both sides of (24) from to for any , we have
Furthermore, it has
Let , we finally obtain
This completes the proof.
3.3. Reachability analysis
Theorem 2: If there exist matrices , scalar , satisfying
with
for ,, Then the states of closed-loop IT2 fuzzy system (12) can be driven into the domain:
with .
Proof: Choose the following Lyapunov function:
Then we have
Denote . From the sliding function (9), we have
For , it has
Following the similar methods in (18) and (19), we can easily derive
Moreover, combining (32) and (35), one obtains
Under condition (28), it follows from (36) that
where is described in Theorem 2. If , we can conducted from (29) that
Taking expectations on both sides of the inequalities (38), it has
which means that the closed-loop IT2 fuzzy system (12) can be driven into the domain .
3.4. Solving algorithm
Theorem 3: If there exist matrices , , positive scalar , , satisfying
with
then the closed-loop IT2 fuzzy system is stochastically stable, and the system states will be driven into the domain simultaneously.
Proof: We just need to prove that the conditions (13),(14),(28),(29) can be ensured by conditions (40),(41).
Letting and , we can obtain (13) and (28) by using (40) via the Schur complement. Condition (14) in Theorem 1 is ensured by condition (29) Theorem 2, for condition (29) implies that
where . Since , is ensured. Moreover, by applying Schur complement to (41), condition (29) is ensured.
We use CCL algorithm to solve the feasibility problem (40-41), it can be converted into the minimization problem:
where .
Remark 2. So far, the addressed SMC problem has been studied for IT2 fuzzy system subject to deception attack by utilizing the torus-event-triggering mechanism. The solvability of the investigated problem has been cast into the feasibility of certain linear matrix inequalities. The required SMC law can be designed by solving the proposed optimization problem. In comparison to those existing literature where SMC method is used, this paper tries to combine the torus-event-triggering mechanism with SMC technique, to help enhance the robustness of the system against malicious attacks. The main merits of our proposed algorithm in comparison to those existing ones can be highlighted as follows: 1) the torus-event-triggering mechanism adopted in this paper could effectively mitigate the influence of the abnormal data resulting from deception attacks; and 2) the sliding mode control conception is utilized in our paper, which makes the designed controller has a strong robustness against to both external disturbances and internal uncertainties.
4. Simulation
In this part, the effectiveness of the proposed control law will be verified by a mass-spring-damper system.
Consider the following mass-spring-damper system
Let and , system (44) can be represented as
The system parameters are given as . Assume that with . Under the condition , the nonlinear function satisfies , where , . The membership functions can be calculated by the following functions:
Then we obtain the membership functions
The lower and upper membership functions are defined as
Consider the variable , the system (45) can be approximated via the following two T-S fuzzy rules:
Rule 1: If is ‘Small’, Then
Rule 2: If is ‘Big’, Then
with
Set the sampling period as 0.2s, we obtain the following matrices:
and we set that . Then the overall IT2 fuzzy system can be expressed as
Note that here we adopted zero-order hold (ZOH) method to transform a continuous-time system into a discrete-time one. The principle of the ZOH method is based on the assumption that the continuous-time input signal remains constant within each sampling interval. This means that the value of the continuous-time signal is held constant until the next sampling instant occurs.
The lower and upper membership functions of the controller are chosen as and for . In this example, the membership functions of system and controller , are determined by the parameter , , and .
The triggering parameters are given as , , and we set the attack probability . The sliding surface parameter is and the deception attacks signal is designed as . By using Theorem 3, the controller gains are calculated as .
Assuming that the initial states are , Figure 1 shows the triggering instants under the torus-event-triggering mechanism. The occurrences of the deception attacks are depicted in Figure 2, where represents that the deception attacks occur. As is shown in Figure 3–4, the control law proposed in this paper can ensure the stability of the IT2 fuzzy system under the deception attacks and the sliding variable is shown in Figure 5.
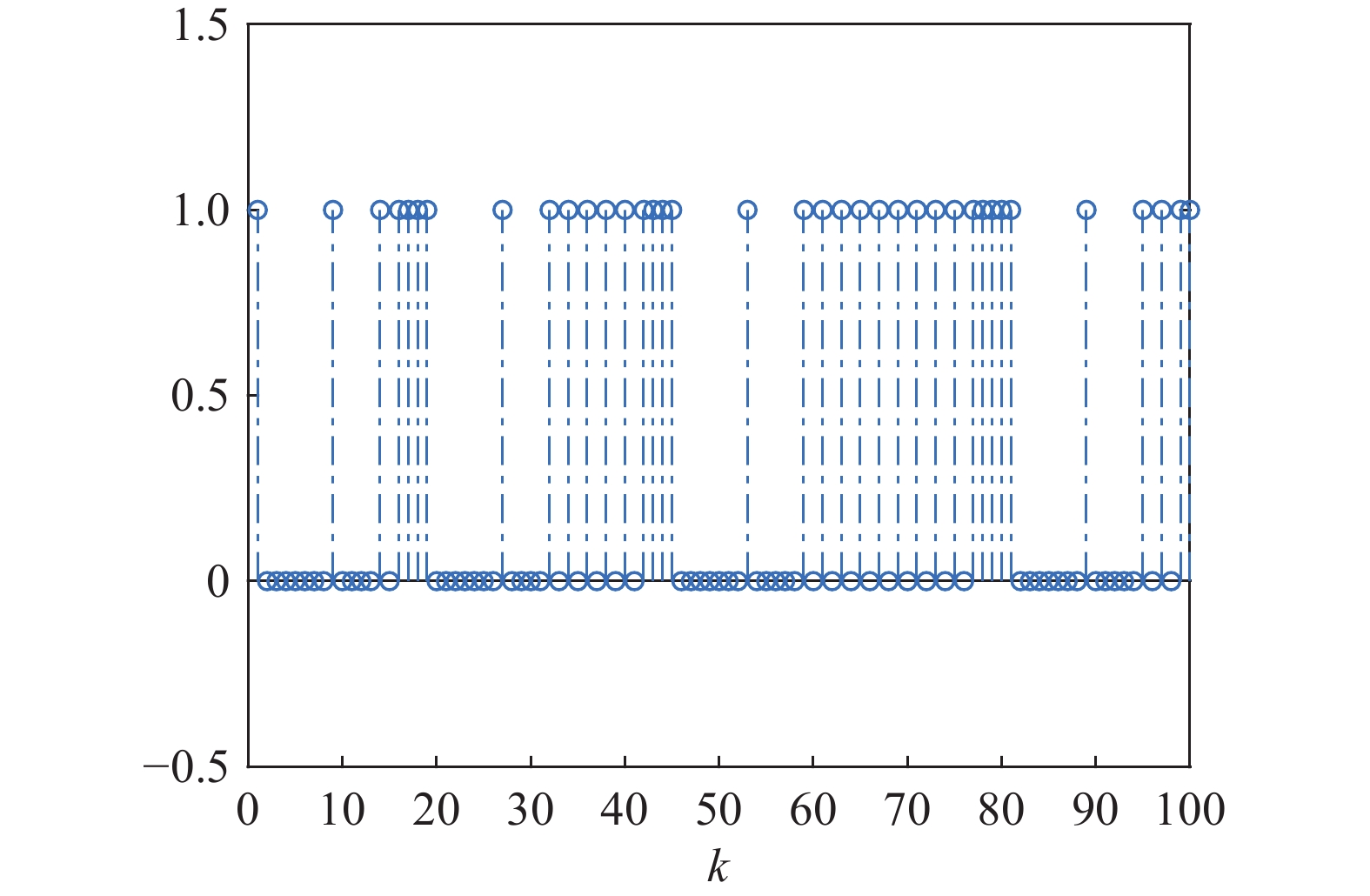
Figure 1. Triggering instants under Torus-Event-Triggering Mechanism.
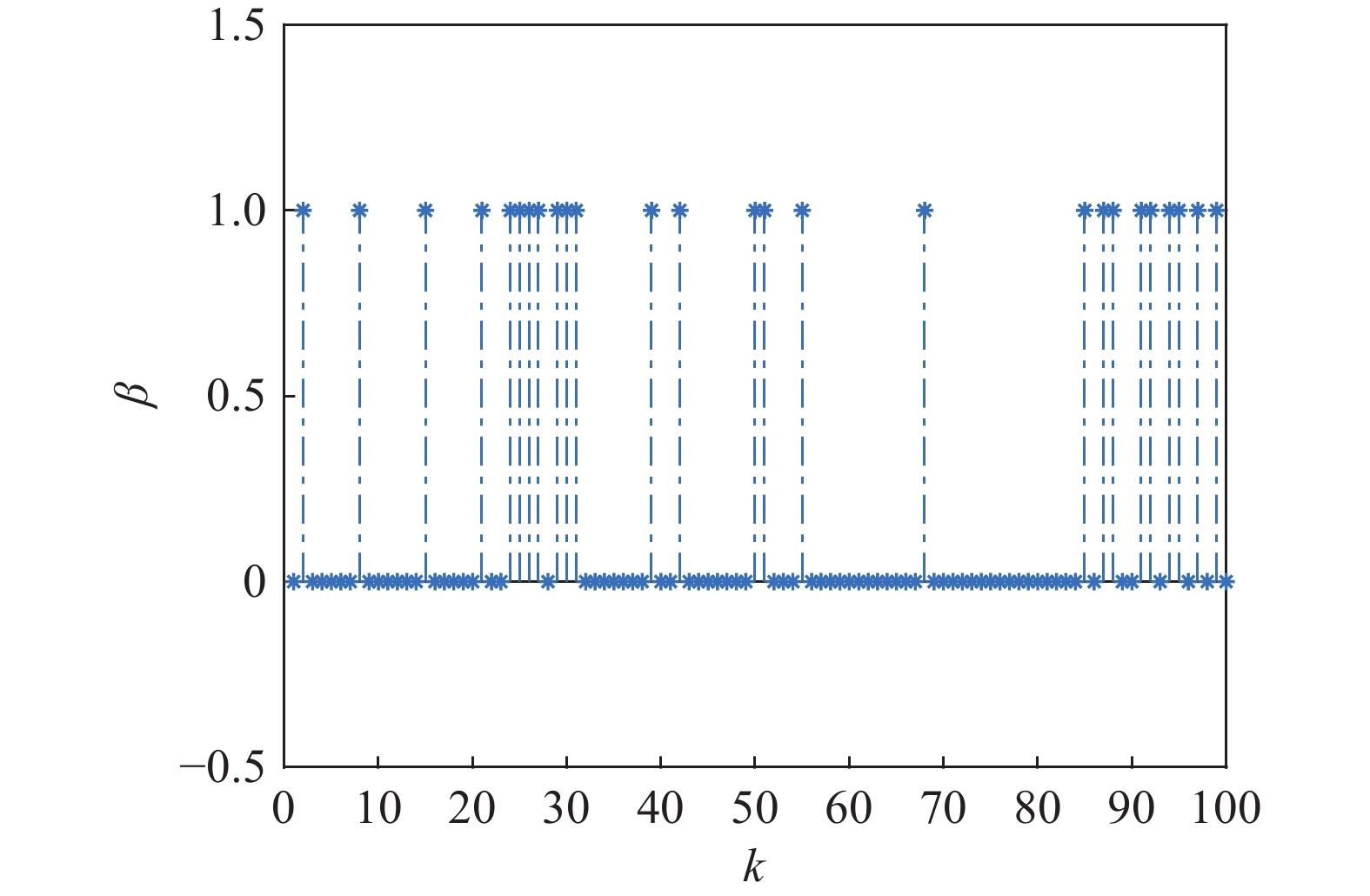
Figure 2. The deception attacks.
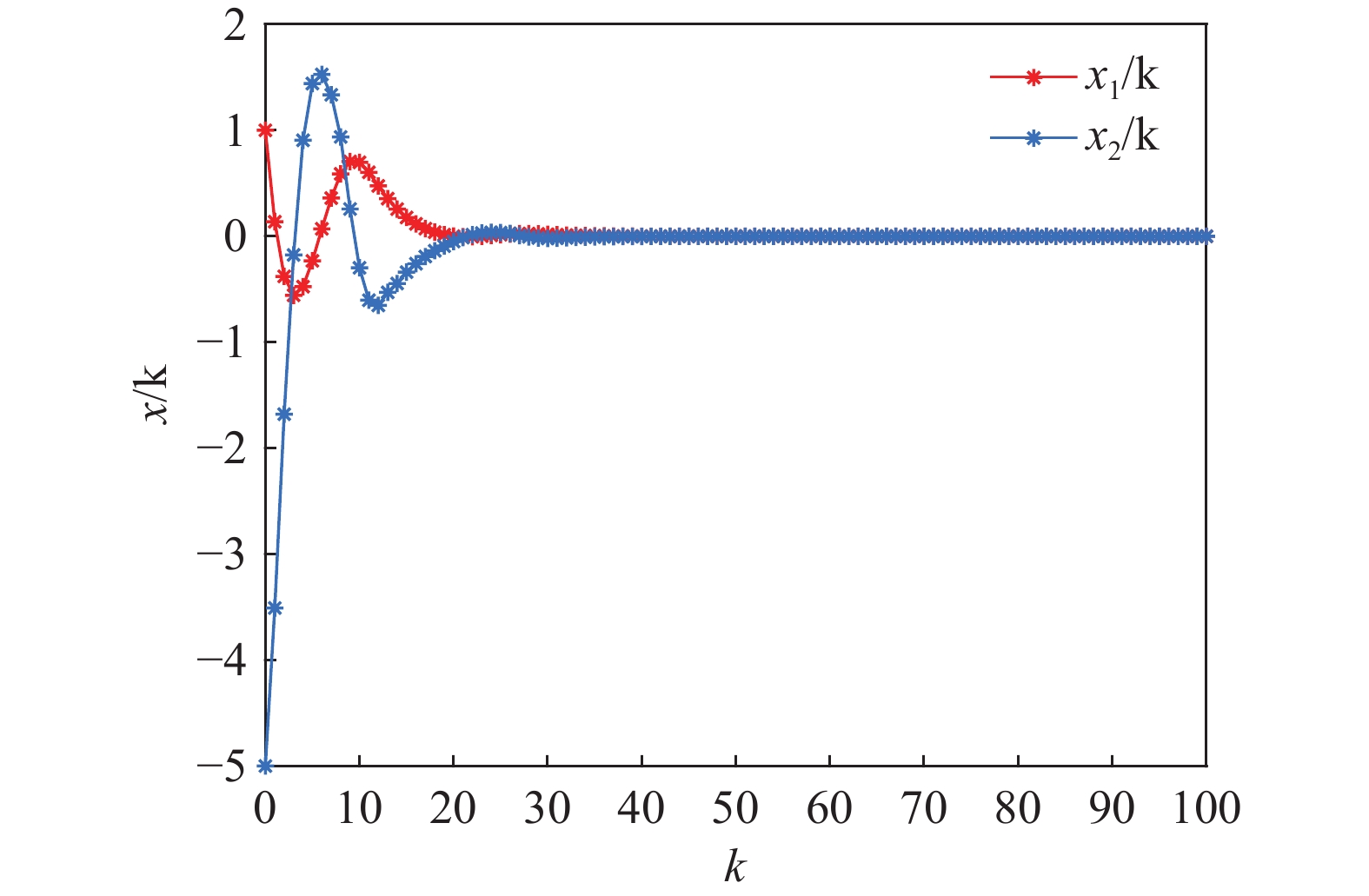
Figure 3. The curve of the system state .
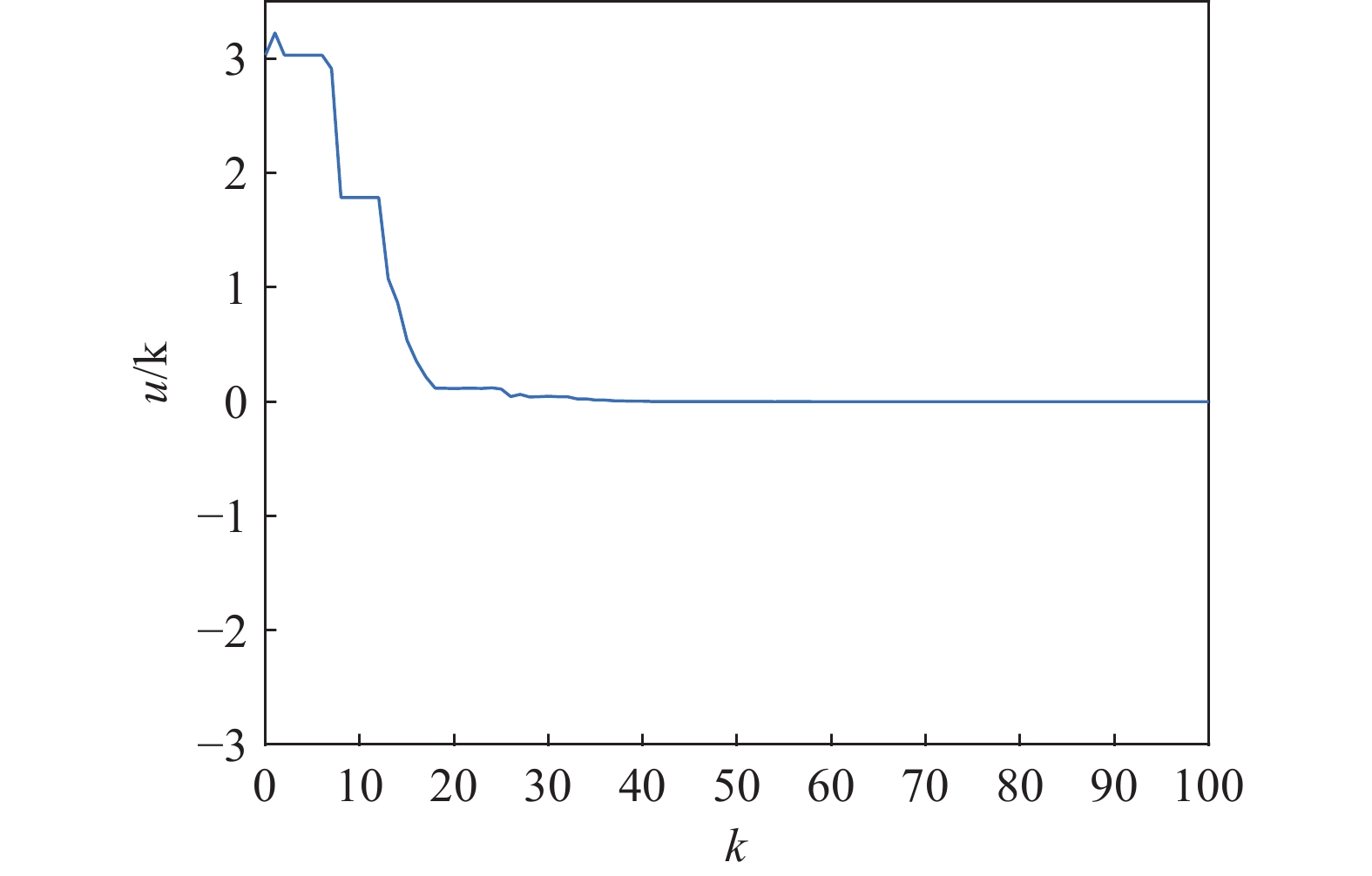
Figure 4. The curve of the control signal .
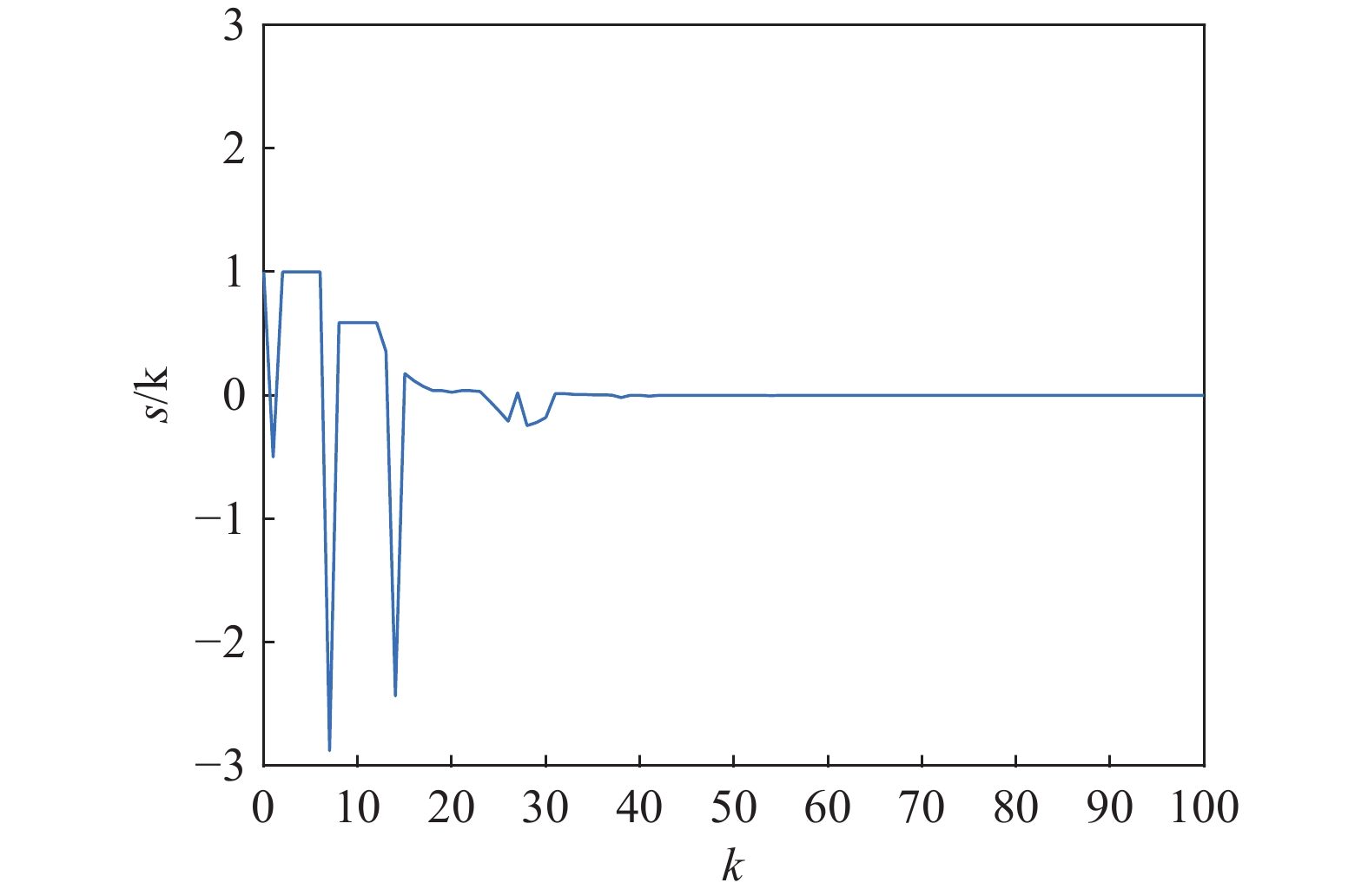
Figure 5. The curve of the sliding variable .
5. Conclusion
This paper has designed the security controller based on SMC technique for IT2 T-S fuzzy system under deception attacks. The torus-event-triggering scheme has been used to decrease the frequency of data transmission and overcome the shortcomings of conventional unilateral-event- triggering strategy. A sliding mode controller has been proposed to ensure the stochastic stability of the closed-loop system and the reachability of the prescribed sliding surface. The effectiveness of the proposed method has been illustrated by a simulation example. In the future work, we will focus on the sliding mode control for different systems subject to different attacks.
Author Contributions: Liu Xingwang: Elaboration of the structure of the paper, Methodology, Investigation, Simulation, Writing-original draft; Ling Zhi: Elaboration of the structure of the paper, Investigation, Methodology, Writing-original draft, Writing —review & editing; Zhang Yang: Reading and correction of the whole paper. All authors have read and agreed to the published version of the manuscript.
Funding: This research received no external funding.
Data Availability Statement: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest.
Acknowledgments: The authors would like to express their sincere thanks to the Editor and the anonymous reviewers for their helpful comments and suggestions that help improve our manuscript.

References
- Zadeh, L. A. Fuzzy sets. Inf. Control, 1965, 8: 338−353. doi: 10.1016/S0019-9958(65)90241-X
- Bellman, R. E.; Zadeh, L. A. Decision-making in a fuzzy environment. Manage. Sci., 1970, 17: 141−164. doi: 10.1287/mnsc.17.4.B141
- Russo, F. Fuzzy systems in instrumentation: Fuzzy signal processing. IEEE Trans. Instrum. Meas., 1996, 45: 683−689. doi: 10.1109/19.492809
- Pedrycz, W. Fuzzy sets in pattern recognition: Methodology and methods. Pattern Recognit., 1990, 23: 121−146. doi: 10.1016/0031-3203(90)90054-O
- Pedrycz, W.
Fuzzy Control and Fuzzy Systems , 2nd ed.; Research Studies Press Ltd: Taunton, 1993. - Fantuzzi, C.; Rovatti, R. On the approximation capabilities of the homogeneous Takagi-Sugeno model. In
Proceedings of IEEE 5th International Fuzzy Systems ,New Orleans ,LA ,USA ,11 September 1996 ; IEEE: New York, 1996; pp. 1067–1072. doi: 10.1109/FUZZY.1996.552326 - Zeng, K.; Zhang, N. Y.; Xu, W. L. A comparative study on sufficient conditions for Takagi-Sugeno fuzzy systems as universal approximators. IEEE Trans. Fuzzy Syst., 2000, 8: 773−780. doi: 10.1109/91.890337
- Sheng, L.; Ma, X. Y. Stability analysis and controller design of interval type-2 fuzzy systems with time delay. Int. J. Syst. Sci., 2014, 45: 977−993. doi: 10.1080/00207721.2012.743056
- Lam, H. K.; Li, H. Y.; Deters, C.; et al. Control design for interval type-2 fuzzy systems under imperfect premise matching. IEEE Trans. Ind. Electron., 2014, 61: 956−968. doi: 10.1109/TIE.2013.2253064
- Pan, Y. N.; Li, H. Y.; Zhou, Q. Fault detection for interval type-2 fuzzy systems with sensor nonlinearities. Neurocomputing, 2014, 145: 488−494. doi: 10.1016/j.neucom.2014.05.005
- Lam, H. K.; Seneviratne, L. D. Stability analysis of interval type-2 fuzzy-model-based control systems. IEEE Trans. Syst. Man Cybern. B Cybern., 2008, 38: 617−628. doi: 10.1109/TSMCB.2008.915530
- Li, H. Y.; Wu, C. W.; Shi, P.; et al. Control of nonlinear networked systems with packet dropouts: Interval type-2 fuzzy model-based approach. IEEE Trans. Cybern., 2015, 45: 2378−2389. doi: 10.1109/TCYB.2014.2371814
- Xiao, B.; Lam, H. K.; Zhong, Z. X.; et al. Membership-function-dependent stabilization of event-triggered interval type-2 polynomial fuzzy-model-based networked control systems. IEEE Trans. Fuzzy Syst., 2020, 28: 3171−3180. doi: 10.1109/TFUZZ.2019.2957256
- Zhao, T.; Xiao, J.; Han, L.; et al. Static output feedback control for interval type-2 T-S fuzzy systems based on fuzzy Lyapunov functions. Asian J. Control, 2014, 16: 1702−1712. doi: 10.1002/asjc.850
- Zhang, Z. N.; Niu, Y. G.; Chen, B. Static output feedback sliding mode control under rice fading channel: An interval type-2 fuzzy modelling method. IET Control Theory Appl., 2020, 14: 3230−3239. doi: 10.1049/iet-cta.2020.0878
- Yang, Y. K.; Niu, Y. G.; Lam, H. K. Sliding-mode control for interval type-2 fuzzy systems: Event-triggering WTOD scheme. IEEE Trans. Cybern., 2023, 53: 3771−3781. doi: 10.1109/TCYB.2022.3163452
- Li, H. Y.; Wang, J. H.; Lam, H. K.; et al. Adaptive sliding mode control for interval type-2 fuzzy systems. IEEE Trans. Syst. Man Cybern. Syst., 2016, 46: 1654−1663. doi: 10.1109/TSMC.2016.2531676
- Zhang, Z. N.; Niu, Y. G.; Cao, Z. R.; et al. Security sliding mode control of interval type-2 fuzzy systems subject to cyber attacks: The stochastic communication protocol case. IEEE Trans. Fuzzy Syst., 2021, 29: 240−251. doi: 10.1109/TFUZZ.2020.2972785
- Ti, B. Z.; Li, G. Y.; Zhou, M.; et al. Resilience assessment and improvement for cyber-physical power systems under typhoon disasters. IEEE Trans. Smart Grid, 2022, 13: 783−794. doi: 10.1109/TSG.2021.3114512
- Wang, X.; Han, S. S.; Yang, L. Y.; et al. Parallel internet of vehicles: ACP-based system architecture and behavioral modeling. IEEE Internet Things J., 2020, 7: 3735−3746. doi: 10.1109/JIOT.2020.2969693
- Yao, F.; Ding, Y. L.; Hong, S. G.; et al. A survey on evolved LoRa-based communication technologies for emerging internet of things applications. Int. J. Network Dyn. Intell., 2022, 1: 4−19. doi: 10.53941/ijndi0101002
- Bao, G. Y.; Ma, L. F.; Yi, X. J. Recent advances on cooperative control of heterogeneous multi-agent systems subject to constraints: A survey. Syst. Sci. Control Eng., 2022, 10: 539−551. doi: 10.1080/21642583.2022.2074169
- Wen, P. Y.; Li, X. R.; Hou, N.; et al. Distributed recursive fault estimation with binary encoding schemes over sensor networks. Syst. Sci. Control Eng., 2022, 10: 417−427. doi: 10.1080/21642583.2022.2063203
- Ding, D. R.; Han, Q. L.; Xiang, Y.; et al. A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing, 2018, 275: 1674−1683. doi: 10.1016/j.neucom.2017.10.009
- Pasqualetti, F.; Dorfler, F.; Bullo, F. Attack detection and identification in cyber-physical systems. IEEE Trans. Automat. Control, 2013, 58: 2715−2729. doi: 10.1109/TAC.2013.2266831
- Mousavinejad, E.; Yang, F. W.; Han, Q. L.; et al. A novel cyber attack detection method in networked control systems. IEEE Trans. Cybern., 2018, 48: 3254−3264. doi: 10.1109/TCYB.2018.2843358
- Pan, Y. N.; Wu, Y. M.; Lam, H. K. Security-based fuzzy control for nonlinear networked control systems with DoS attacks via a resilient event-triggered scheme. IEEE Trans. Fuzzy Syst., 2022, 30: 4359−4368. doi: 10.1109/TFUZZ.2022.3148875
- Ding, D. R.; Wang, Z. D.; Wei, G. L.; et al. Event-based security control for discrete-time stochastic systems. IET Control Theory Appl., 2016, 10: 1808−1815. doi: 10.1049/iet-cta.2016.0135
- Ding, D. R.; Wang, Z. D.; Han, G. L.; et al. Security control for discrete-time stochastic nonlinear systems subject to deception attacks. IEEE Trans. Syst. Man Cybern. Syst., 2018, 48: 779−789. doi: 10.1109/TSMC.2016.2616544
- Zhu, S. X.; Tian, E. G.; Xu, D. H.; et al. An adaptive torus-event-based H ∞ controller design for networked T-S fuzzy systems under deception attacks. Int. J. Robust Nonlinear Control, 2022, 32: 3425−3441. doi: 10.1002/rnc.5957
- Zhang, H. Y.; Zhao, N.; Wang, S. Y.; et al. Improved event-triggered dynamic output feedback control for networked T-S fuzzy systems with actuator failure and deception attacks. IEEE Trans. Cybern., 2023, 53: 7989−7999. doi: 10.1109/TCYB.2023.3264820
- Wang, X. L.; Sun, Y.; Ding, D. R. Adaptive dynamic programming for networked control systems under communication constraints: A survey of trends and techniques. Int. J. Network Dyn. Intell., 2022, 1: 85−98. doi: 10.53941/ijndi0101008
- Cao, Z. R.; Niu, Y. G.; Karimi, H. R. Dynamic output feedback sliding mode control for Markovian jump systems under stochastic communication protocol and its application. Int. J. Robust Nonlinear Control, 2020, 30: 7307−7325. doi: 10.1002/rnc.5172
- Ding, D. R.; Wang, Z. D.; Han, Q. L.; et al. Neural-network-based output-feedback control under round-robin scheduling protocols. IEEE Trans. Cybern., 2018, 49: 2372−2384. doi: 10.1109/TCYB.2018.2827037
- Zhang, Z. N.; Niu, Y. G.; Lam, H. K. Sliding-mode control of T-S fuzzy systems under weighted try-once-discard protocol. IEEE Trans. Cybern., 2019, 50: 4972−4982. doi: 10.1109/TCYB.2019.2941870
- Qu, F. R.; Zhao, X.; Wang, X. M.; et al. Probabilistic-constrained distributed fusion filtering for a class of time-varying systems over sensor networks: A torus-event-triggering mechanism. Int. J. Syst. Sci., 2022, 53: 1288−1297. doi: 10.1080/00207721.2021.1998721
- An, W. J.; Zhao, P. F.; Liu, H. J.; et al. Distributed multi-step subgradient projection algorithm with adaptive event-triggering protocols: A framework of multiagent systems. Int. J. Syst. Sci., 2022, 53: 2758−2772. doi: 10.1080/00207721.2022.2063967
- Yang, J. J.; Ma, L. F.; Chen, Y. G.; et al. L2-L ∞ state estimation for continuous stochastic delayed neural networks via memory event-triggering strategy. Int. J. Syst. Sci., 2022, 53: 2742−2757. doi: 10.1080/00207721.2022.2055192
- Ju, Y. M.; Wei, G. L.; Ding, D. R.; et al. Finite-horizon fault estimation for time-varying systems with multiple fading measurements under torus-event-based protocols. Int. J. Robust Nonlinear Control, 2019, 29: 4594−4608. doi: 10.1002/rnc.4640
- Costa, O. L. V.; Marques, R. P.; Fragoso, M. D.
Discrete-Time Markov Jump Linear Systems ; Springer: London, 2005. doi: 10.1007/b138575







