Downloads
 Download
Download




This work is licensed under a Creative Commons Attribution 4.0 International License.
Article
Security Coordination Control for the Belt Conveyor Systems with False Data Injection Attacks
Lei Ma 1,2, Hao Zhang 1,2, Guoqing Wang 1,2, Chunyu Yang 1,2,*, and Linna Zhou 1,2
1 School of Information and Control Engineering, China University of Mining and Technology, Xuzhou 221116, China
2 Xuzhou Coal Mining Group Co., Ltd, Xuzhou 221116, China
* Correspondence: E-mail: chunyuyang@cumt.edu.cn
Received: 30 July 2024
Accepted: 11 October 2024
Published: 25 March 2025
Abstract: This paper addresses the issue of security coordination control for belt conveyor systems (BCSs) vulnerable to false data injection (FDI) attacks in an industrial Internet of Things scenario. A networked BCSs drive model is established for the first time consisting of flexibly connected dual permanent magnet synchronous motors. Subsequently, a novel security control strategy based on quadratic regulators is proposed to preserve the drive motor synchronization in response to FDI attacks that compromise the signal interaction from sensors to controllers. Afterward, a composite sub-optimal security coordination controller is presented based on the singular perturbation theory and the corresponding solution approach, recognizing the two-time-scale dynamics inherent to motor systems. The proposed criteria both eliminate ill-conditioned numerical issues and assure system stability. Furthermore, simulations exhibit the advantages and physical experiments confirm the efficiency of the developed algorithms.
Keywords:
belt conveyor systems dual-motor drive optimal control singular perturbation theory cyber attacks1. Introduction
Belt conveyor systems (BCSs) are essential to transfer numerous materials in mining, metallurgy, ports, and manufacturing industries, which substantially improves production efficiency, conserves labor, and promotes process automation [1−2]. Due to the powerful driving force and high torque output, the dual-motor-drive module (DMDM) is usually picked to elevate the efficiency of conveying large or heavy cargo handling jobs [3]. To maintain system performance, DMDM is required to operate at synchronous speed and balanced torque in addition to having an efficient power transmission system. Asynchronous speed or imbalanced torque of DMDM causes major threats to machine security and operation stability of BCSs, such as conveyor belt breakage, motor damage, or even production accidents [4]. As such, the enhancement of BCSs operational efficiency and safety heavily relies on the coordination control of DMDM [5].
The coordination control structure of DMDM consists of four control structures, namely the virtual main shaft one [6], the cross-coupling one [7], the parallel one, and the master-slave one [8]. The coordination performance can be severely affected by external disturbances on any device, as the parallel control structure and the master-slave control structure lack coupled control. Therefore, the principle of cross-coupling control has been put forward. The fundamental idea behind cross-coupling control, initially brought forth by Koren [9], is to use the synchronization error as a compensation signal and adjust each motor individually to minimize the errors. Chen presented an adaptive cross-coupling control scheme and studied its stability, which simultaneously ensures stability and strengthens coordination [10]. Zhou designed a hierarchical control strategy that combines cross-coupling control with sliding mode control, thereby significantly reducing synchronization errors and enhancing control performance [11].
More control systems are connected via networks as a result of the industrial internet’s extensive use, and significant wiring necessary for traditional point-to-point control can be alleviated by sharing signals across networks [12−14]. Nevertheless, the networked control system inevitably encounters plenty of cyber attacks, which may lead to a decline in control performance or even system instability[15−18]. By capturing system model parameters and operating data, false data injection (FDI) attacks change the data transmitted via sensor and actuator channels, getting a lot of research attention. A distributed estimation and control approach based on an adaptive mechanism has been proposed by [19] to protect multi-agent systems’ tracking consistency from FDI attacks. A robust model predictive control method has been highlighted by [20] to provide system security against norm-bounded FDI attacks. Using the principles of switching control, [21] broke down the original system into a switching system with several control modes thus establishing a security control strategy against sparse FDI attacks.
It should be noted that existing security control methods cannot be directly used for the BCSs because of ill-conditioned numerical issues caused by the multi-time-scale property (MTTP) of DMDM [22−24], Meng studied the problem of optimal coordinated control of a two-motor system [25], however it cannot provide effective methods to deal with the problem for cyber attacks, and this encourages us to close this gap.
This paper aims to study the safe and coordinated control of belt conveyor systems under FDI attacks, with a particular focus on two key performance indexes: speed synchronization and torque balance. Despite its theoretical significance and practical potential, it poses three foreseeable yet critical difficulties: 1) how to establish a proper attack model to characterize FDI attacks occurring on sensors to controllers; 2) how to design an appropriate security control strategy to cope with the adverse effects of FDI attacks. 3) how to construct a reasonable control structure and corresponding algorithm to overcome ill-conditioned numerical issues? As such, it is our main objective to find a satisfactory solution to these three questions.
1) A novel BCSs’ DMDM model based on flexible connected dual permanent magnet synchronous motors is established in the industrial Internet of Things (IIoT) environment.
2) A security coordinated control framework for the BCSs is designed, for the first time, under the cross-coupling structure, which can ensure the synchronization of the drive motors.
3) A singular-perturbation-based algorithm is proposed to solve control gain parameters without numerical stiffness, and the obtained composite controller can guarantee the sub-optimal control performance.
2. Drive model of belt conveyor in the iiot environment
In this paper, the flexible connected dual-motor system is adopted as the driving device of the belt conveyor systems, which includes permanent magnet synchronous motors, rollers, and a flexible conveyor belt. The two motors are connected through the flexible conveyor belt. The specific structure is shown in Figure 1, and the main parameters and symbols of the motor are listed in Table 1. Due to the connection between the motors through the conveyor belt, which is relatively distant, with low coupling and affected by dynamic loads and tension, inconsistencies in torque and speed may occur, leading to conveyor belt failures or even motor damage. Therefore, it is necessary to consider both torque balance and speed consistency.
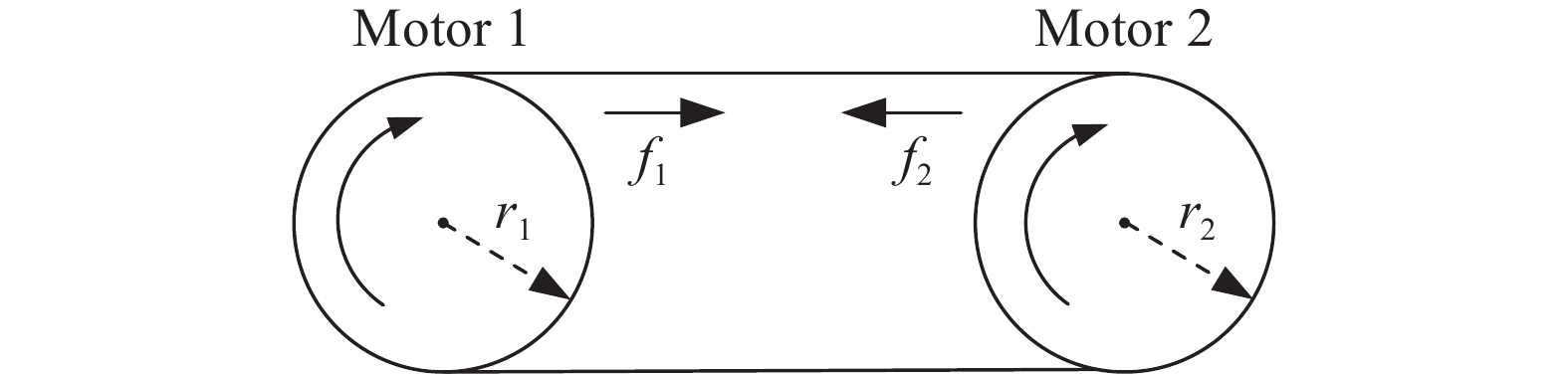
Figure 1. Structure of the flexible connected dual-motor system.
| Variable | Symbol | Unit |
| Given mechanical angular | rad/s | |
| velocity of motor | ||
| Mechanical angular velocity | , | rad/s |
| shaft current | , | A |
| shaft current | , | A |
| Moment of inertia | , | |
| Friction coefficient | , | |
| shaft inductance | , | H |
| Polar logarithm | , | / |
| Stator resistance | , | |
| Permanent magnet flux | , | |
| Electromagnetic | , |
First, analyze the force conditions of the system structure diagram shown in Figure 1. Here, and are the interaction forces due to the belt tension when the speeds of the two motors are inconsistent. and are the radii of wheel 1 and wheel 2 respectively, typically taken as . is the stiffness coefficient of the flexible connected material. According to Hooke’s law, it can be obtained.
Assuming that the loads of the two motors themselves are ,, combined with the coupling characteristics of the flexible coupling of ,, it can be seen that the actual loads of the two motors are respectively
Combining (2) with the mathematical model of the permanent magnet synchronous motor in the coordinate system [26], the mathematical model of the dual permanent magnet synchronous motor with flexible coupling can be obtained. Then the control strategy of is adopted, which not only realizes the maximum torque control, but also obtains the simplified system model.
3. Safety coordination control framework for belt conveyors under fdi network attacks
This section will introduces the design and analysis methods of a sefety coordination controller for a dual-motor driven belt conveyor systems under FDI cyber attacks. Firstly, building upon the conventional cross-coupling control structure, an optimal coordinated control architecture is proposed with the objective of minimizing velocity tracking error and torque synchronization error. However, in practical networked belt conveyor systems, the integrity of data transmission channels can be compromised due to cyber attacks, leading to data anomalies. Therefore, this chapter presents a security coordination control approach where the designed controller mitigates the impact of FDI cyber attacks on the belt conveyor systems. To avoid numerical instability issues during solution, a design methodology for a composite suboptimal sefety coordinated controller is proposed based on singular perturbation theory.
3.1. Optimized Coordinated Control Structure for Belt Conveyor Systems
The drive module of the belt conveyor systems adopt a two-motor cross-coupling control structure as shown in Figure 2, which can not only significantly improve the response speed and dynamic performance of the system, but also strengthen the stability and robustness of the system. In order to take into account the speed consistency and torque balance, the outputs of the speed regulators and the -axis current regulators for both motors are, respectively, designed as follows:
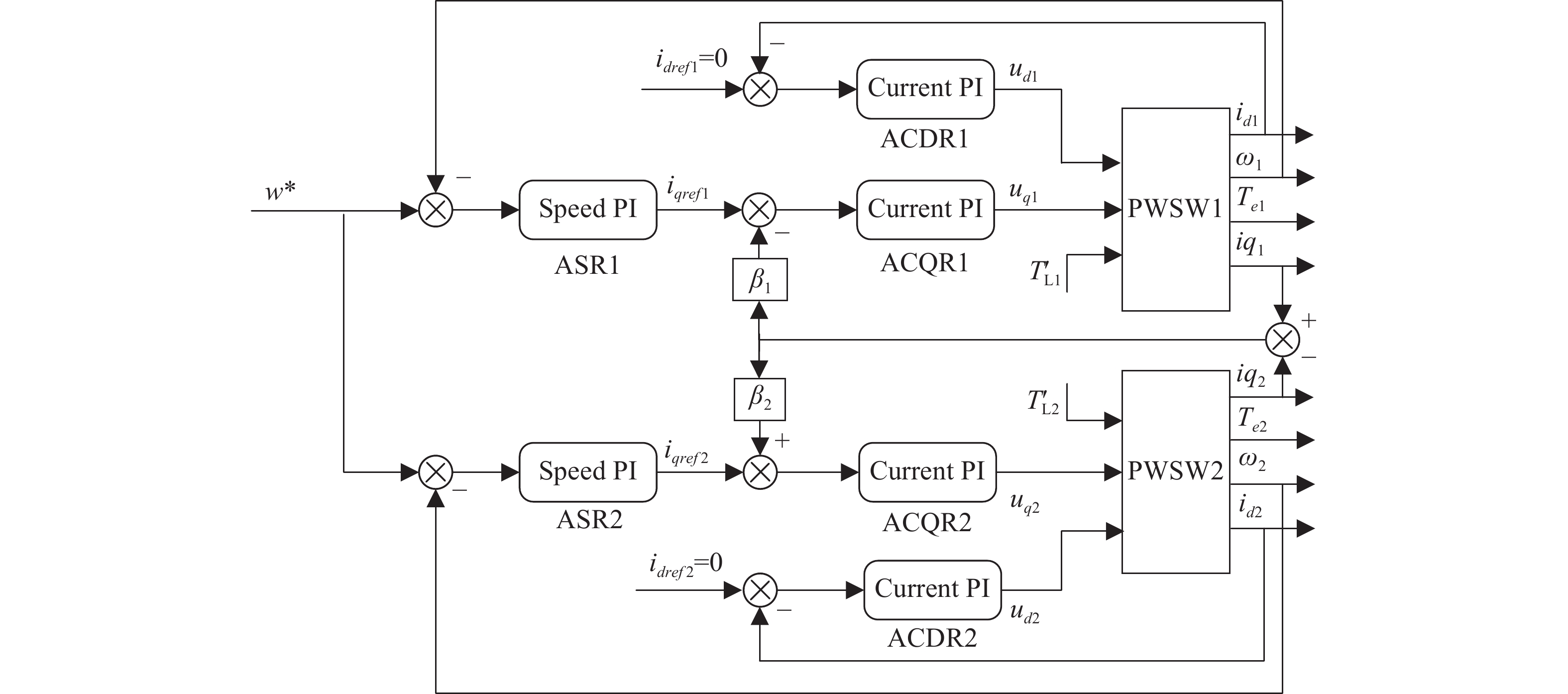
Figure 2. Cross-coupling control structure for Dual-motor systems.
Let
Then
According to (3)-(7),the state-space form of the belt conveyors driven by dual motors can be obtained.
where
The control objective of this section is to ensure consistent speed and torque balance between the two drive motors, thus the system’s outputs are chosen as:
where and are weighting coefficients. The larger the weight factor corresponding to each state variable, the more importance the controller attaches to it.
Therefore, the optimized coordinated control problem of the belt conveyor systems can be formulated as the following LQR problem. [27] where the constant disturbance term does not affect the system structure and hence is not considered.
where
Find the optimal state feedback control that minimizes the following performance index
where, are weight matrices and is a solution of the Riccati equation
Remark 1: and for the coupling feedback adjustment coefficient, the larger their values, the higher the degree of coupling between the motors, the faster the system response when the load changes or external perturbations, but the worse the stability of the system, generally take , this paper take .
3.2. Secure Controller Design under FDI Cyber Attacks
FDI cyber attacks, also known as deception attacks, manipulate the veracity of system data by injecting erroneous control or measurement signals into the networked transmission channels. For belt conveyor systems, exploiting encryption vulnerabilities in the dual-motor system devices, FDI cyber attacks typically manifest in two forms: (1) The data measured by the sensor is injected with false data during the communication process, thus successfully tampering with the data received by the controller. (2) Control commands output by the controller were injected with false data during the communication process, thereby causing the actuator to receive erroneous control commands. This chapter focuses on researching the first type of attack, as illustrated in Figure 3.
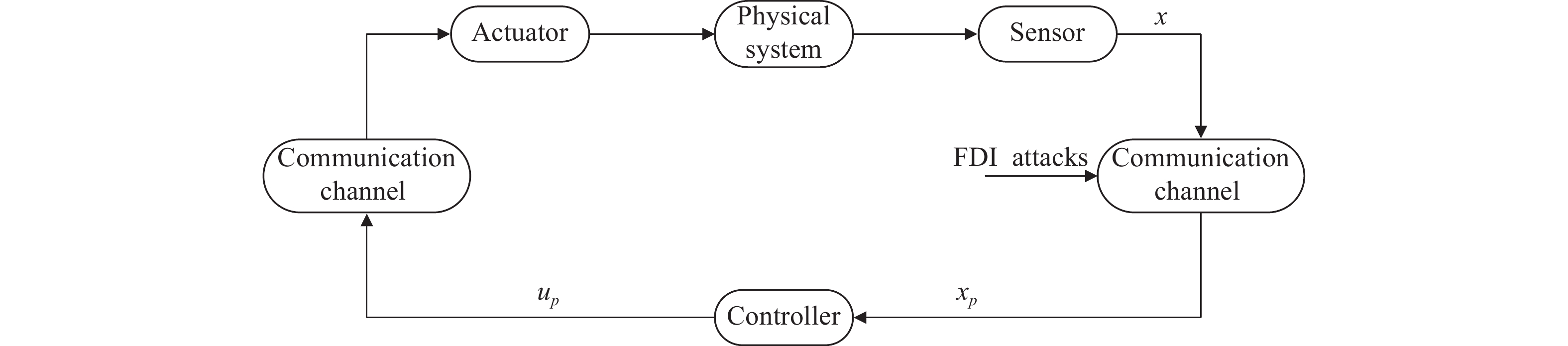
Figure 3. Schematic diagram of FDI attack.
The system state suffers from the FDI cyber attack while being transmitted over the network transmission channel from the sensor to the controller, then the controller acquires the system state as
where is the false system state after the attack, is the attack signal (channel data acquisition) to which the controller is subjected, and F is the attack state matrix, which is able to indicate whether the signal is under attack or not, where an element of 1 indicates that the signal is under attack, and an element of 0 indicates that it is not under attack.
According to (13), there must exist a real matrix such that
According to (14), the belt conveyor systems (10) under FDI cyber attacks can be described as follows:
where is the safety coordination controller to be designed for the belt conveyor system
Transform the safety coordination control problem of system (15) into an LQR problem to enhance the performance of speed consistency and torque balance in DMDM. According to the LQR algorithm, the following performance metrics are proposed.
where, are weight matrices and the state feedback control input is
where P is a solution of the Riccati equation (19)
Remark 2: This chapter focuses exclusively on a specific scenario where the sensor-controller channel is subjected to FDI cyber attacks, with the attack signals linearly correlated with the system state.
3.3. Design and solution of suboptimal safety coordination controller based on singular perturbation theory
Due to the dual-time-scale property of DMDM, designing a controller by solving the corresponding Riccati equations using traditional optimal control theory directly can easily lead to ill-conditioned numerical issues. Therefore, singular perturbation theory [28] is employed to design a composite suboptimal safety coordination controller as depicted in Figure 4.
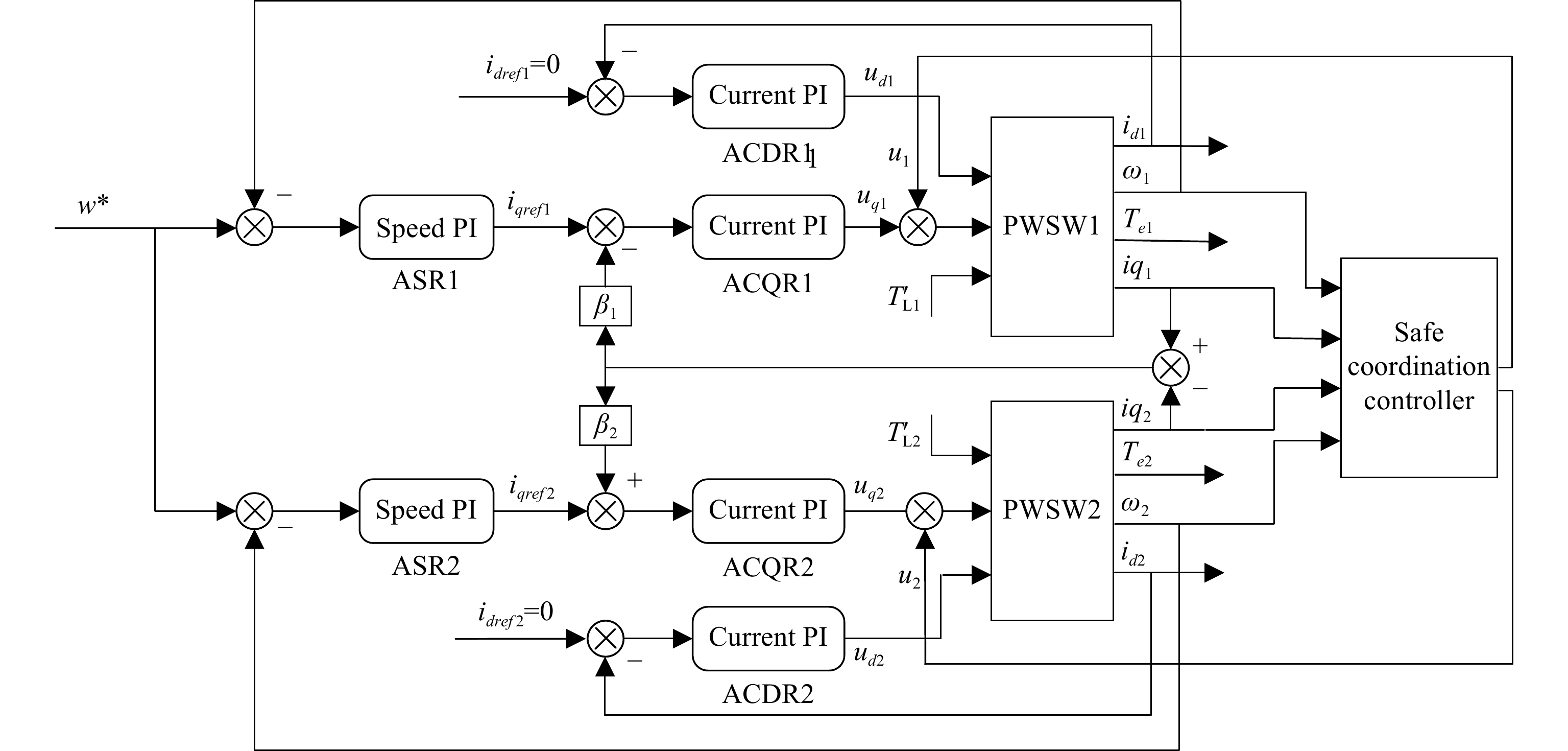
Figure 4. Block diagram of the safety coordination control for a dual-motor driven belt conveyor system.
First, the state space equations are written in the form of a linear singular perturbation system
where is the perturbation parameter.
Since is a reversible matrix, according to singular perturbation theory, system (20) can be decomposed into fast and slow subsystems. The original LQR problem (17) can also be decomposed into LQR problems for the fast subsystem and the slow subsystem, with the specific decomposition as follows.
(1) Slow subsystem
Find the optimal controller such that the slow subsystem performance index is minimized
where
(2) Fast subsystems
Find the optimal controller such that the fast subsystem performance index is minimized
where
The feedback gain can be obtained by solving the Riccati equations corresponding to the fast and slow subsystems separately.
Finally, the combined control is obtained and used in the original system to realize the optimized coordinated control of the system. The composite suboptimal control is
Remark 3: Due to the dual time scale characteristic of the motor system, the singular perturbation theory can avoid the numerical solution difficulties caused by the time scale difference by using its unique mathematical framework and analytical tools. This not only helps to optimize the performance of the control system, but also improves the reliability and applicability in practical engineering applications. Therefore, the design of a safety coordination controller using singular perturbation theory not only effectively solves the dual time scale problem of the original system, but also ensures that the system achieves a higher level in terms of dynamic response and stability.
4. Simulation verification
The safety coordination controller proposed in this paper is applied to belt conveyor systems, and the feasibility and effectiveness of the method is verified by simulation in this section. In the belt conveyors, and . The motor parameters are shown in Table 2.The PI parameters of speed regulator and current regulator are .
| Symbol | Value | Unit |
| , | ||
| , | ||
| , | ||
| , | / | |
| , | ||
| , |
First, the optimized coordination controller for the belt conveyor system without any attack is solved. After adding the optimized coordination controller, the synchronization error of the speed and torque of the drive motor can be effectively reduced [25]. However, the state data collected by the system can be tampered after the system suffers from FDI cyber attacks. By choosing an appropriate attack matrix , a previously stable system with an optimized coordination controller can be destroyed. Figure 5 and Figure 6 illustrate the speed and current variations of the two drive motors during the FDI cyber attacks. It can be observed that the speed and current of the system start to oscillate and diverge within a short period of time, which eventually leads to system crash. This indicates that the FDI cyber attacks can disrupt the normal operation of the system by injecting false data, thus damaging the performance and safety of the system.
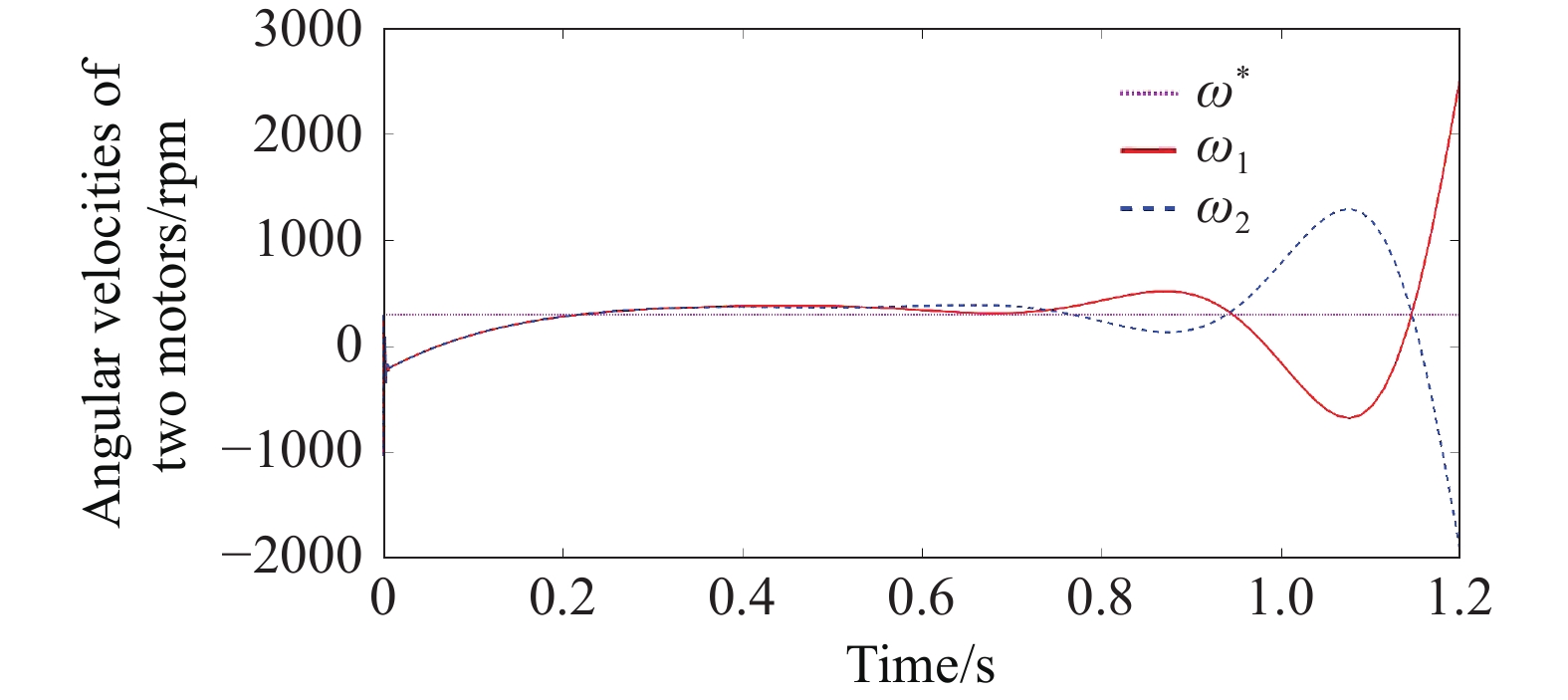
Figure 5. Angular velocity of two motors under FDI attack.
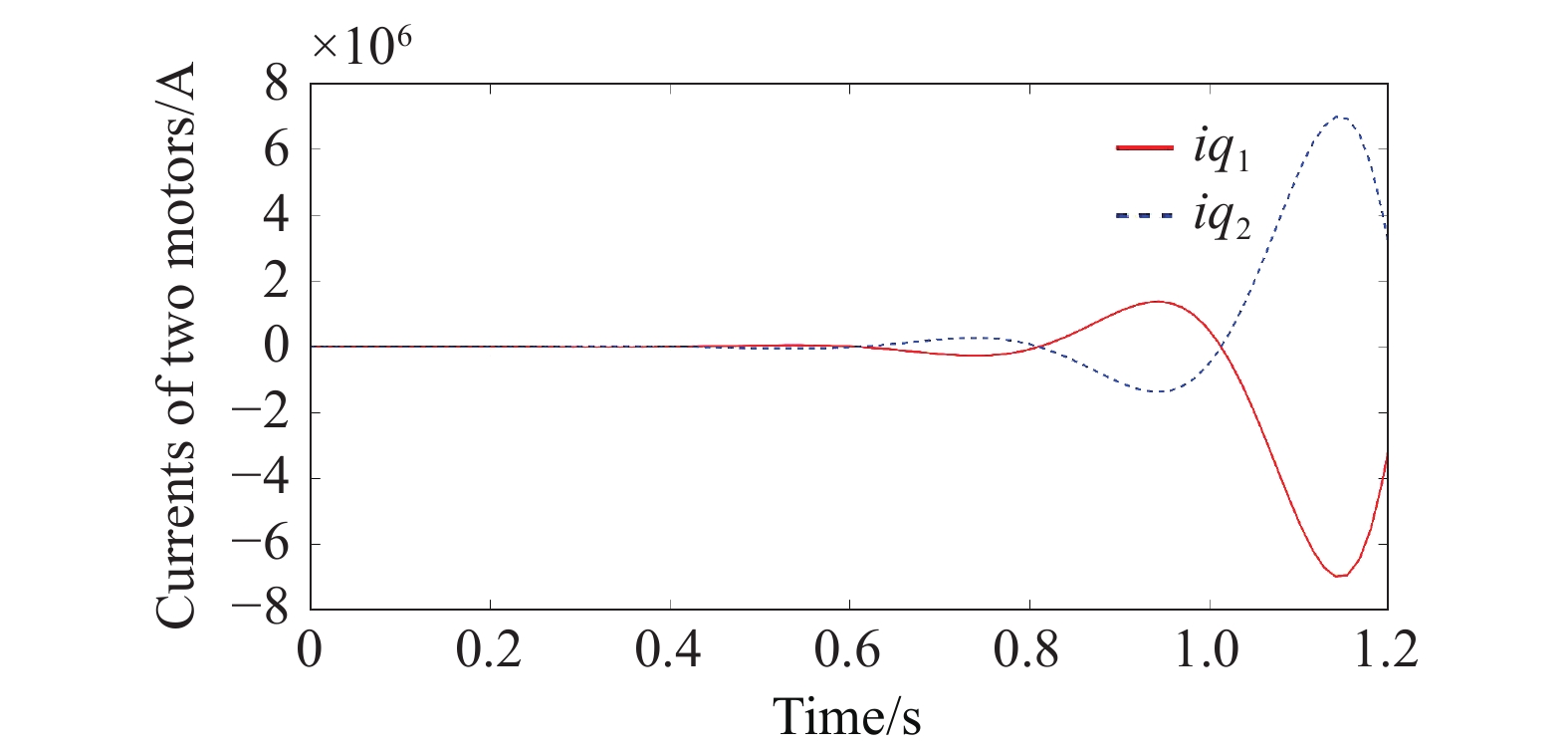
Figure 6. Current of two motor under FDI attack.
According to the method proposed in this paper, a suboptimal safety coordination controller is designed based on the optimal control theory and singular perturbation theory. In this paper, , , the Riccati equations shown in (25), (26) are solved, and finally the suboptimal safety coordination controller (27) can be obtained which is later added to the above belt conveyor system that has been attacked by FDI cyber. Figure 7 and Figure 8 show the changes of the speed and current of the drive motor when the system is added with the safety coordination controller. It can be seen that the speed of the two motors can be adjusted for a period of time to achieve speed synchronization and torque synchronization. It can be seen that the design of the safety coordination controller can effectively resist the impact of FDI cyber attacks.
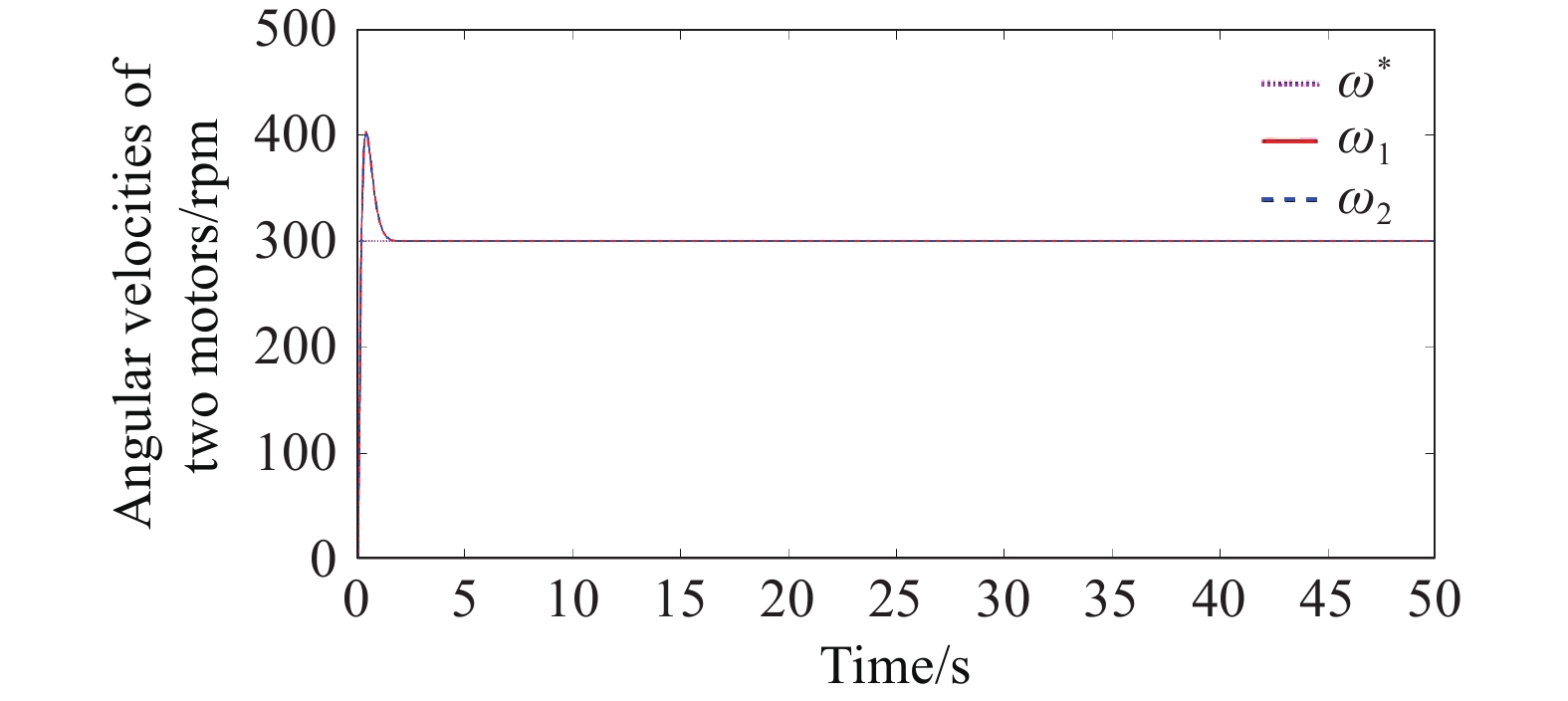
Figure 7. Angular speed of two motors under the safety coordination Controller.
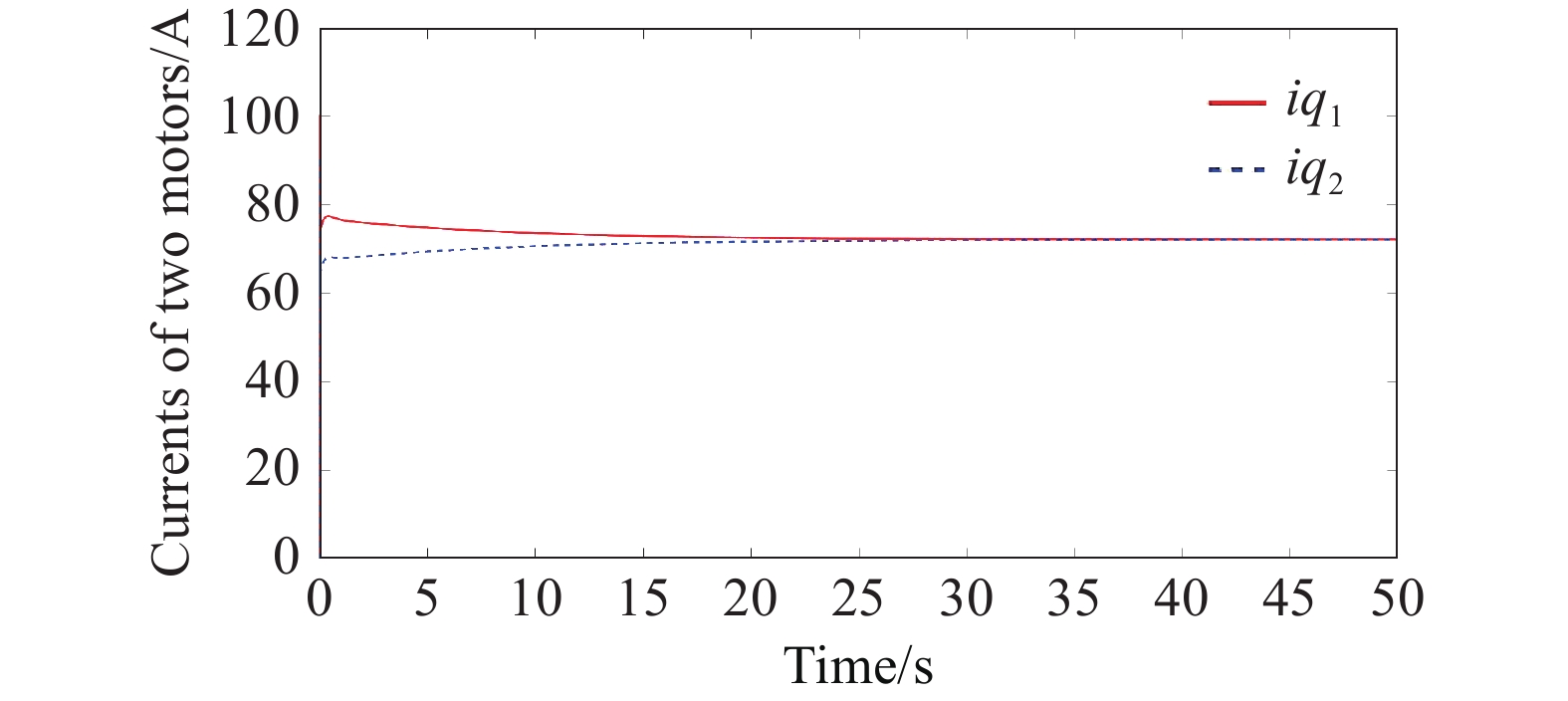
Figure 8. Current of two motors under safety coordination controller.
Finally, in order to test the effect of load change on the system performance, after the system is stabilized, it is set that the load of the drive motor 1 changes at , and the load of the drive motor 2 changes at . Figure 9 and Figure 10 give the changes of the current and speed of the two drive motors when their loads are changed, and the results show that the designed safety coordination controller can still achieve synchronization of current and speed when the loads are changed. After a period of regulation, the two motors can still achieve speed synchronization and torque synchronization.
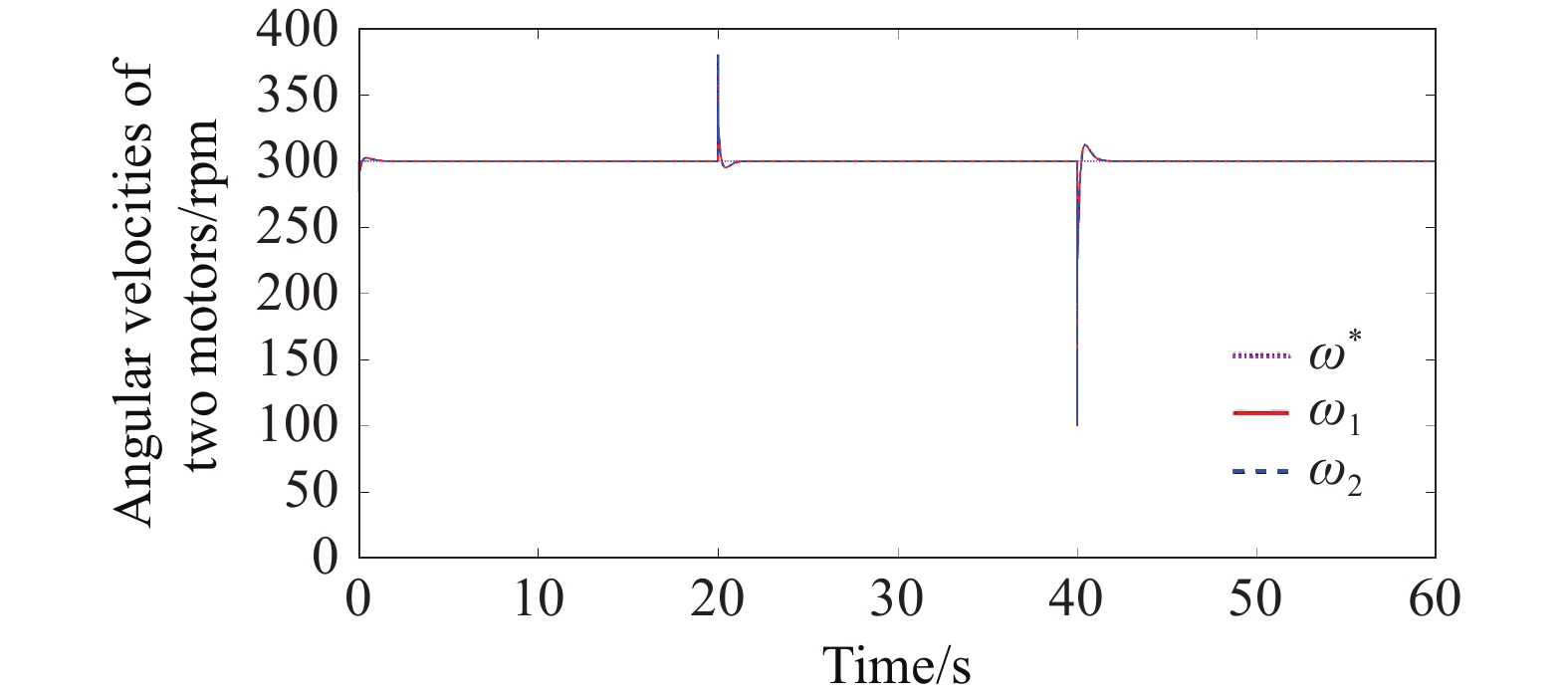
Figure 9. Angular speed of two motors in case of sudden load change under safety coordination controller.
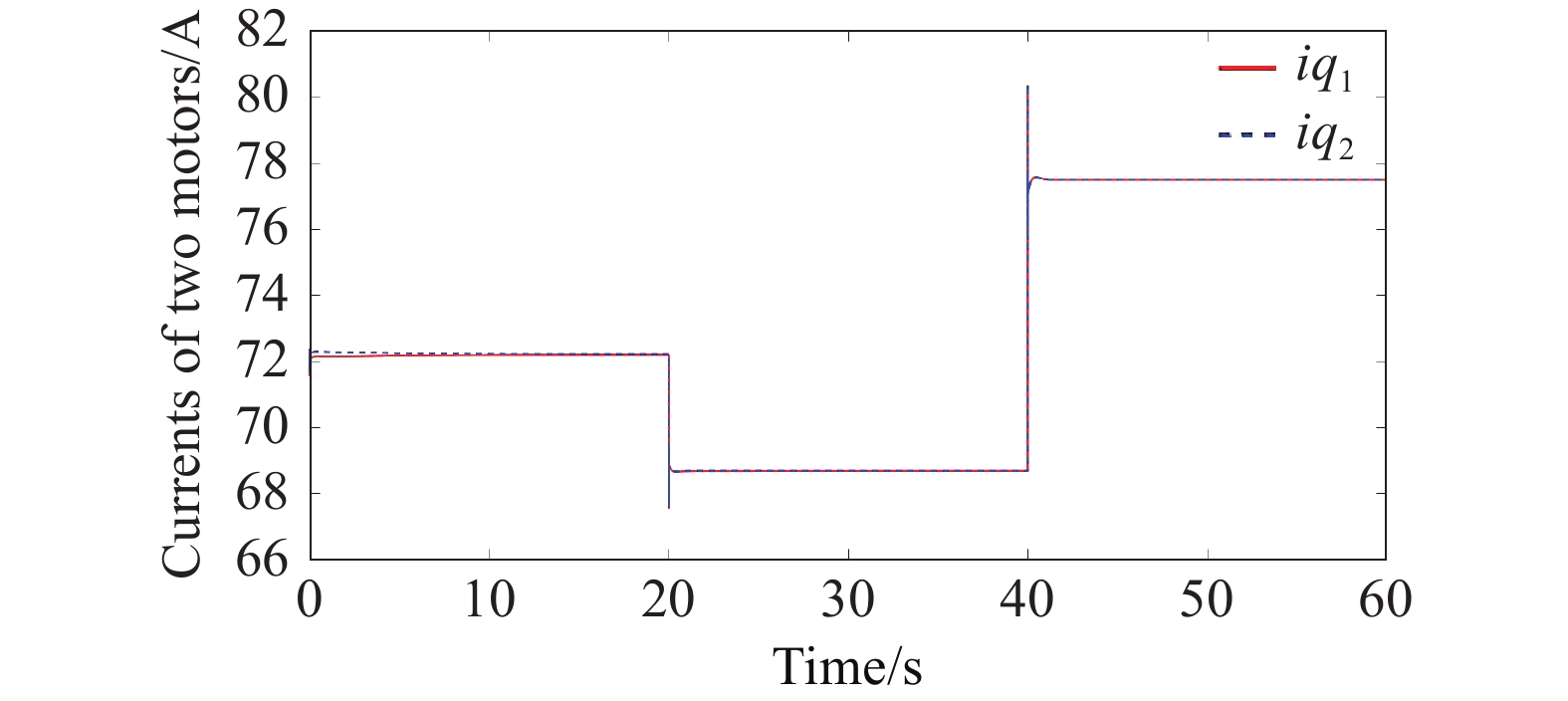
Figure 10. Current of two motors in case of sudden load change under safety coordination controller.
5. Experimentation
In this section, a networked belt conveyor experimental platform as shown in Figure 11 is used for experimental validation. This experimental platform can realize the optimized coordinated control of the belt conveyor system, in addition to simulating the impact of cyber attacks on the system. The networked belt conveyor experimental platform mainly includes hardware equipment and software algorithms. The hardware system is built based on the dSPACE system, and the main hardware parts include the dual motor-driven belt conveyor mechanical experimental device, MircoLabBox controler, converter, voltage regulator, adapter plate, and the upper computer. microLabBox is one of the hardware components of the a dSPACE system. As the controller of the experimental platform, it is responsible for the compilation and running of the algorithms to verify and transmit the control signals through the IO interface. The software system is based on Matlab/Simulink and the ControlDesk software of the dSPACE system. The simulated cyber environment and the control algorithms for the belt conveyor system are implemented in Matlab/Simulink and compiled into C language in MicroLabBox. The upper computer interface for experimental operation, parameter modification and data monitoring was drawn in ControlDesk software.
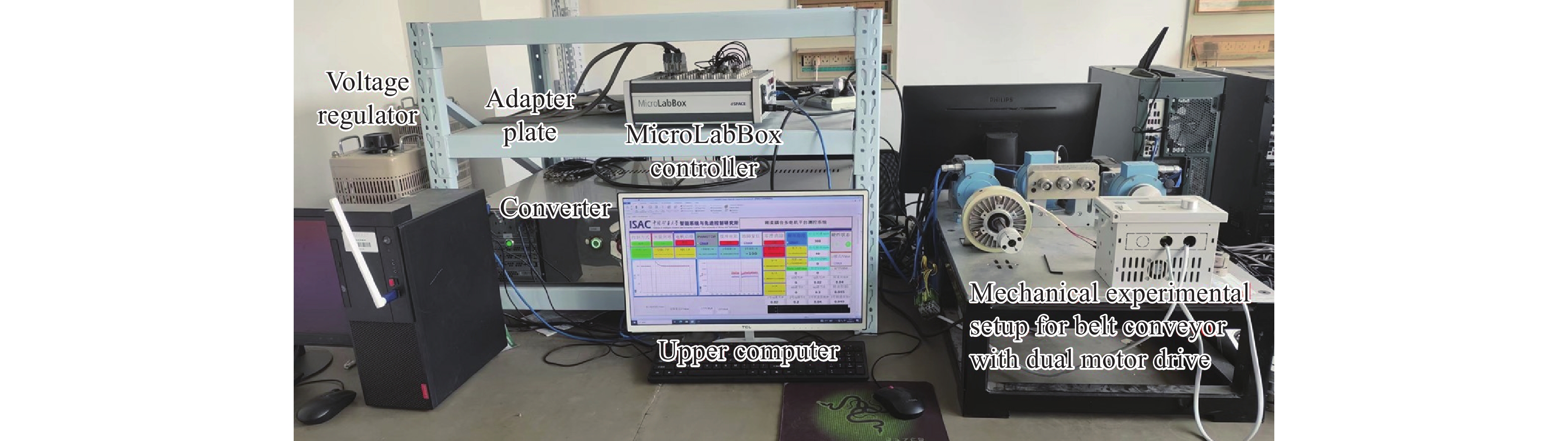
Figure 11. The hardware system of the networked belt conveyor experimental platform.
In the experiment, the effectiveness of the designed safety coordination controller against the impacts of FDI cyber attacks was validated. Figure 12 and Figure 13 illustrate the drive motor speeds and currents of the belt conveyor system under FDI attacks after integrating the secure coordinated controller. It is evident that, after a period of adjustment, the system achieved speed synchronization and torque synchronization. Therefore, the designed safety coordination controller can effectively avoid the impact of FDI cyber attacks, enhancing the security and reliability of the system.
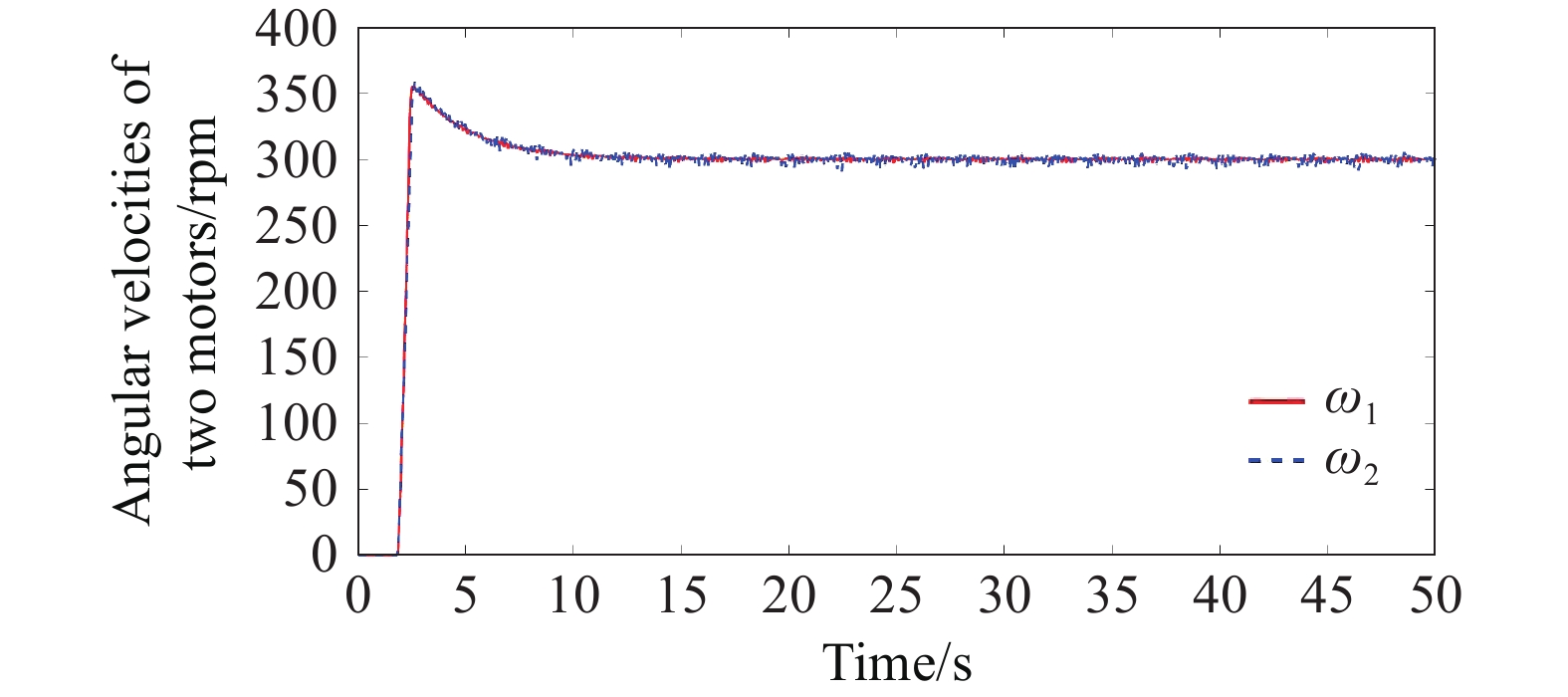
Figure 12. Angular speed of two motors under the safety coordinated Controller.
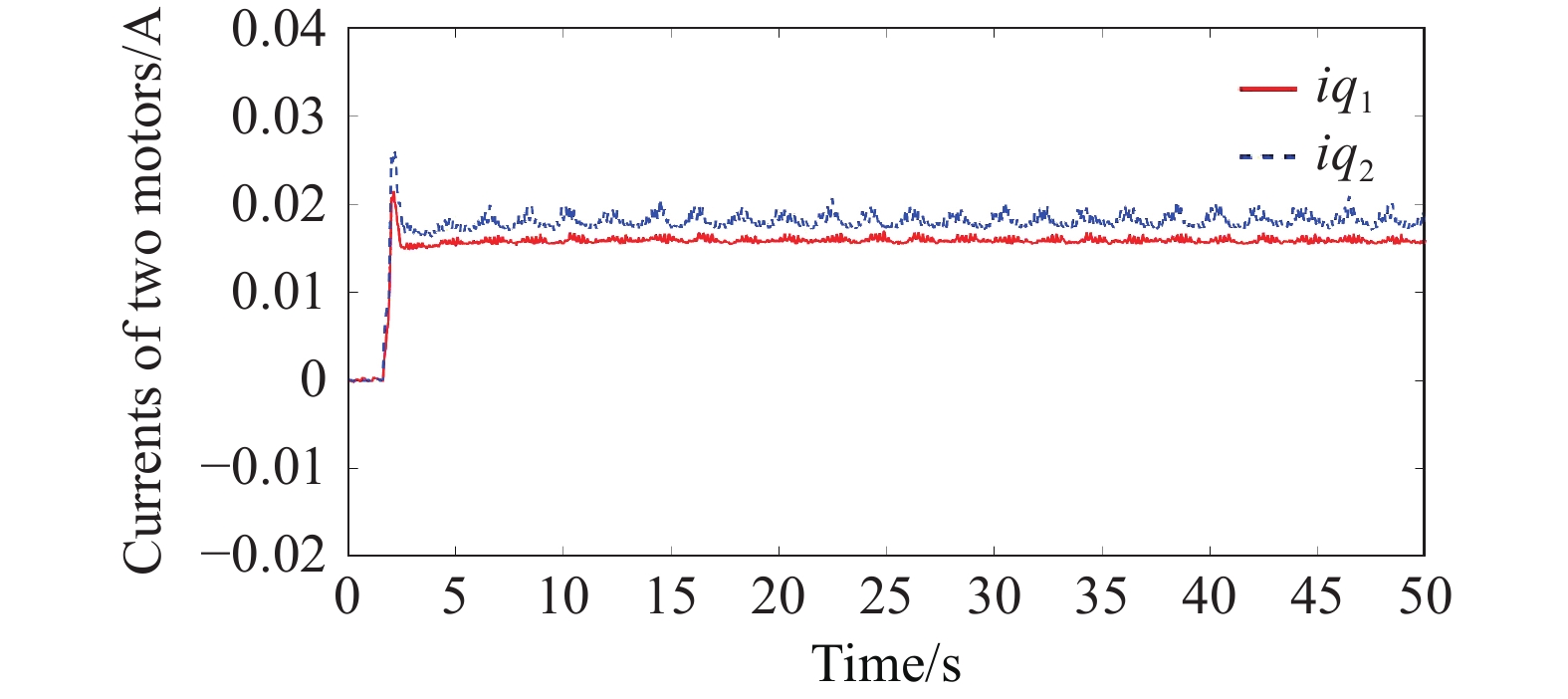
Figure 13. Current of two motors under safety coordination controller.
6. Summary
In this article, the problem of safe coordinated control of belt conveyor systems under FDI cyber attacks is investigated. Firstly, a drive control model of networked belt conveyor based on flexibly coupled dual motors is established, and then a safe coordinated controller is designed by combining the LQR algorithm for the case of the system suffering from FDI cyber attacks. Considering that the motor system has dual time scales, a suboptimal composite safety coordination controller is designed by applying the singular uptake theory. This not only effectively avoids the pathological numerical problem, but also reduces the dimension of the system and simplifies the computation to some extent. The final simulation and experimental ones demonstrate that this composite security coordination controller effectively counteracts the effects brought by FDI cyber attacks. For different forms of cyber attacks and different security control methods, more in-depth research will be conducted in the future.
Author Contributions: Ma Lei: Data analysis and Writing. Zhang Hao: Formal analysis. Wang Guoqing: Validation. Yang Chunyu and Zhou Linna: Methodology.
Funding: National Key Research and Development Program of China (2022YFB3304700), National Natural Science Foundation of China (62203448, 62273350,62373362), China Postdoctoral Science Foundation (2023M732968, 2024T170751).
Data Availability Statement: Not available.
Conflicts of Interest: The authors declare no conflict of interest.
Acknowledgments: Our research was partly financed by Xuzhou Coal Mining Group Co.,Ltd, thanks very much for their experiment devices and equipment.

References
- He, D.J.; Pang, Y.S.; Lodewijks, G. Green operations of belt conveyors by means of speed control. Appl. Energy, 2017, 188: 330−341. doi: 10.1016/j.apenergy.2016.12.017
- Mu, Y.F.; Yao, T.A.; Jia, H.J.; et al. Optimal scheduling method for belt conveyor system in coal mine considering silo virtual energy storage. Appl. Energy, 2020, 275: 115368. doi: 10.1016/j.apenergy.2020.115368
- Masaki, M.S.; Zhang, L.J.; Xia, X.H. A design approach for multiple drive belt conveyors minimizing life cycle costs. J. Cleaner Prod., 2018, 201: 526−541. doi: 10.1016/j.jclepro.2018.08.040
- Andrejiova, M.; Grincova, A.; Marasova, D. Measurement and simulation of impact wear damage to industrial conveyor belts.
Wear 2016 ,368 –369 , 400–407. doi: 10.1016/j.wear.2016.10.010 - He, D.J.; Pang, Y.S.; Lodewijks, G.; et al. Healthy speed control of belt conveyors on conveying bulk materials. Powder Technol., 2018, 327: 408−419. doi: 10.1016/j.powtec.2018.01.002
- Zhang, X.Y.; Liu, H.Z.; Fu, Y.; et al. Virtual shaft control of DFIG-based wind turbines for power oscillation suppression. IEEE Trans. Sustain. Energy, 2022, 13: 2316−2330. doi: 10.1109/TSTE.2022.3194164
- Chen, C.S.; Chen, L.Y. Robust cross-coupling synchronous control by shaping position commands in multiaxes system. IEEE Trans. Ind. Electron., 2012, 59: 4761−4773. doi: 10.1109/TIE.2011.2182012
- Liang, Z.P.; Hu, S.D.; Li, Z.; et al. Research on master–slave windings motor drive system and control strategy. IEEE Trans. Ind. Electron., 2023, 70: 88−98. doi: 10.1109/TIE.2022.3156171
- Koren, Y. Cross-coupled biaxial computer control for manufacturing systems. J. Dyn. Syst. Meas. Control, 1980, 102: 265−272. doi: 10.1115/1.3149612
- Chen, W.; Wang, D.D.; Geng, Q.; et al. Robust adaptive cross-coupling position control of biaxial motion system. Sci. China Technol. Sci., 2016, 59: 680−688. doi: 10.1007/s11431-015-5988-8
- Zou, S.C.; Zhao, W.Z. Synchronization and stability control of dual-motor intelligent steer-by-wire vehicle. Mech. Syst. Signal Proc., 2020, 145: 106925. doi: 10.1016/j.ymssp.2020.106925
- Zhang, X.M.; Han, Q.L.; Ge, X.H.; et al. Networked control systems: A survey of trends and techniques. IEEE/CAA J. Autom. Sin., 2020, 7: 1−17. doi: 10.1109/JAS.2019.1911651
- Zhang, X.M.; Han, Q.L.; Yu, X.H. Survey on recent advances in networked control systems. IEEE Trans. Ind. Inf., 2016, 12: 1740−1752. doi: 10.1109/TII.2015.2506545
- Lu, A.Y.; Yang, G.H. Distributed secure state estimation for linear systems against malicious agents through sorting and filtering. Automatica, 2023, 151: 110927. doi: 10.1016/j.automatica.2023.110927
- Ma, L.; Chu, Z.; Yang, C.Y.; et al. Recursive watermarking-based transient covert attack detection for the industrial CPS. IEEE Trans. Inf. Forensics Secur., 2023, 18: 1709−1719. doi: 10.1109/TIFS.2023.3251857
- Wang, F.; Wang, Z.D.; Liang, J.L.; et al. Locally minimum-variance filtering of 2-D systems over sensor networks with measurement degradations: A distributed recursive algorithm. IEEE Trans. Cybern., 2022, 52: 996−1008. doi: 10.1109/TCYB.2020.2989207
- Wang, F.; Wang, Z.D.; Liang, J.L.; et al. Recursive locally minimum-variance filtering for two-dimensional systems: When dynamic quantization effect meets random sensor failure. Automatica, 2023, 148: 110762. doi: 10.1016/j.automatica.2022.110762
- Wang, F.; Wang, Z.D.; Liang, J.L.; et al. Recursive state estimation for two-dimensional shift-varying systems with random parameter perturbation and dynamical bias. Automatica, 2020, 112: 108658. doi: 10.1016/j.automatica.2019.108658
- Huang, X.; Dong, J.X. Reliable leader-to-follower formation control of multiagent systems under communication quantization and attacks. IEEE Trans. Syst. Man Cybern. Syst., 2020, 50: 89−99. doi: 10.1109/TSMC.2019.2894946
- Wang, J.; Ding, B.C.; Hu, J.C. Security control for LPV system with deception attacks via model predictive control: A dynamic output feedback approach. IEEE Trans. Autom. Control, 2021, 66: 760−767. doi: 10.1109/tac.2020.2984221
- Wu, C.W.; Yao, W.R.; Pan, W.; et al. Secure control for cyber-physical systems under malicious attacks. IEEE Trans. Control Network Syst., 2022, 9: 775−788. doi: 10.1109/TCNS.2021.3094782
- Zhao, J.G.; Yang, C.Y.; Gao, W.N. Reinforcement learning based optimal control of linear singularly perturbed systems. IEEE Trans. Circuits Syst. II Express Briefs, 2022, 69: 1362−1366. doi: 10.1109/TCSII.2021.3105652
- Forni, P.; Angeli, D. Perturbation theory and singular perturbations for input-to-state multistable systems on manifolds. IEEE Trans. Autom. Control, 2019, 64: 3555−3570. doi: 10.1109/TAC.2018.2882165
- Ma, L.; Yang, C.Y.; Wang, G. Q.; et al. H∞ control for a class of two-time-scale cyber–physical systems: An asynchronous dynamic event-triggered protocol. IEEE Trans. Cybern., 2023, 53: 5013−5023. doi: 10.1109/TCYB.2022.3159370
- Yang, C.Y.; Meng, F.Y.; Zhang, H.J.; et al. Optimal coordinated control for speed tracking and torque synchronization of rigidly connected dual-motor systems. IEEE/ASME Trans. Mechatron., 2023, 28: 2609−2620. doi: 10.1109/TMECH.2023.3242663
- Kommuri, S.K.; Park, Y.; Lee, S.B. Online compensation of mechanical load defects with composite control in PMSM drives. IEEE/ASME Trans. Mechatron., 2021, 26: 1392−1400. doi: 10.1109/TMECH.2020.3019507
- Lewis, F.L.; Vrabie, D.; Syrmos, V.L.
Optimal Control , 3rd ed.; John Wiley& Sons: Hoboken, 2012. - Kokotović, P.; Khalil, H.K.; O’reilly, J.
Singular Perturbation Methods in Control: Analysis and Design ; SIAM: Philadelphia, 1999.







